@Dusk Is DUSK’s tech defensible, or is it one zk-upgrade away from being outpaced?
DUSK pitches itself as a privacy-first, compliance-ready Layer-1 designed to host regulated financial activity and real-world assets (RWAs). That positioning has moved from theoretical marketing into concrete partnerships and product-level work: an updated whitepaper, public collaboration with regulated Dutch exchange NPEX and integrations around Chainlink interoperability, plus a focused roadmap for privacy-preserving tokenized securities and an EVM-compatible execution environment. Those facts matter because DUSK is not starting from vapor — it’s building with institutional rails in mind, not just crypto-native privacy theater.
To judge defensibility you need a framework that separates three layers:
(1) the cryptographic primitives (how privacy is actually achieved),
(2) the protocol and economic architecture (consensus, finality, auditability, upgradeability),
(3) the product and market moat (customers, regulatory bridges, integrations, real revenues). DUSK attempts to defend across all three. It uses zero-knowledge proofs (ZKPs) and specialized privacy primitives to enable shielded state transitions and smart contracts while offering “compliant privacy” features — meaning auditors and regulated parties can still obtain required views without exposing raw ledger data. That technical direction is explicitly different from pure anonymity coins; DUSK trades absolute transparency for policy-friendly confidentiality. The team’s updated whitepaper and product pages describe ZKPs and zero-knowledge tokens as core execution primitives rather than add-ons. Those design choices tighten the narrative: DUSK isn’t competing with Monero for anonymity, it’s competing to be the Fabric/Hyperledger replacement for tokenized securities.
But cryptographic building blocks are a fast-moving frontier. ZK primitives that were exotic in 2020 became mainstream by 2023–2024. Improvements in proof systems, proving performance, and tooling (Halo, PLONK variants, recursive proof composition, STARKs) change the competitive map quickly. A privacy chain’s core advantage — being able to express complex business logic under confidentiality guarantees with reasonable cost and latency — rests on which ZK stack it uses and how easily it can swap or layer new ZK tech. DUSK’s whitepaper and updates show a living protocol that recognizes ZK primitives as central. That’s necessary but not sufficient: the real test is how modular the stack is, how the team manages proof-system upgrades, and whether the design locks in certain tradeoffs (e.g., heavy precomputation, large verifier keys, or on-chain verifier costs) that newer proof systems can beat. If DUSK’s architecture allows incremental ZK upgrades without breaking composability or on-chain semantics, it remains competitive. If the architecture binds core semantics to a now-dated proof family, it becomes fragile the day a cheaper/more expressive proof family becomes pervasive. The updated whitepaper suggests active maintenance of the ZK stack, but the detail that determines long-term defensibility is the protocol’s modularity for proof engines — a development area DUSK must keep funding and prioritizing.
Consensus and economic design are the second corner where defensibility must be earned. Privacy introduces special operational risks: typical soft-fork patching and node debugging are harder when you cannot see the raw state easily, and privacy at scale can change attacker incentives (data collection becomes valuable off-chain). DUSK’s approach couples privacy primitives with a Proof-of-Stake consensus and governance model tailored to institutional use — staking economics aimed at predictable finality and validator reliability. Predictability matters for institutional counterparties that cannot tolerate the probabilistic finality or complex reorg windows some L2 designs expose. Public materials from DUSK emphasize “predictable performance” and auditability as selling points; in practice, predictability plus verifiable on-demand audit views creates a product that regulators can evaluate and approve faster than a pure privacy coin. That is a defensible market niche if executed.
The product moat — partnerships, regulatory entanglements, and developer ecosystem — is where DUSK currently looks strongest relative to pure cryptography. The NPEX partnership is not window dressing: it brings licensed market infrastructure and a route to tokenize regulated securities and a euro-backed electronic money token (EURQ) onchain. Chainlink CCIP and data integrations strengthen interoperability and cross-chain reach for those tokenized assets. Partnerships like these create stickiness that purely cryptographic superiority cannot erase overnight. If NPEX, market makers, custodians, and compliance tooling standardize on DUSK primitives for tokenized securities, the network acquires an operational moat — counterparties, legal templates, and onboarding flows that newcomers must replicate. Building such a commercial moat is slow but defensible because it sits at the intersection of tech, law, and market practice where expertise matters.
Still, the question remains: is DUSK’s tech itself defensible against a future where a different chain adopts a dramatically improved ZK system and matches compliance features faster? The answer is nuanced. A purely technical competitor that innovates a more efficient ZK engine and can also layer compliance features could, in theory, displace DUSK’s technical lead. But replacing a live institutional integration is harder than swapping out a library. Institutions will weigh migration costs, legal agreements, custody linkages, and the safety of existing asset rails. Therefore, DUSK’s defensibility is partly technical and partly institutional inertia. If DUSK locks in real-world issuance and liquidity (e.g., tens or hundreds of millions in RWAs), it gains the kind of network effects that blunt purely technical attacks. That is why the Dusk–NPEX–Chainlink axis is a crucial strategic bet: it converts cryptography into business advantage.
To make the debate more concrete, consider a realistic case study: the EURQ pilot and tokenized SME securities on NPEX. DUSK, NPEX, and partners like Cordial and Quantoz have announced pilots to tokenize regulated securities and an electronic euro token. In a pilot where a licensed exchange issues tokenized SME bonds on DUSK, the chain must satisfy three simultaneous constraints: regulatory auditability, atomic settlement guarantees for market integrity, and confidentiality of borrower and investor identities from unrelated onlookers. The pilot’s success depends on DUSK delivering low-latency settlement for exchange trades, cryptographic proofs that allow selective disclosure to regulators, and reliable off-chain custody and oracle connectivity. If any of these fail — for instance, if proving costs cause settlement delays or if the selective disclosure mechanism leaks data — the pilot dies or becomes legally untenable. Early public reporting suggests DUSK has engineered for these constraints and signed real contracts that commit counterparties to using their stack, which de-risks the product beyond a research paper. This is real commercial progress that raises the bar for competitors.
Contrast DUSK’s trajectory with other privacy approaches to see where risks and strengths lie. Zcash and Monero take the privacy-first route focused on user anonymity; their use case is mostly transactional privacy for retail users. Aztec and other ZK-centric rollups pushed ZK execution earlier but were built primarily for DeFi contexts rather than regulated securities. DUSK instead embeds privacy semantics into asset issuance and compliance tooling — a different product problem. That means DUSK’s technical choices (for example, how it encodes regulatory claims, auditor keys, and compliance channels) are specialized. Those specialized choices are harder to port: a new chain could adopt the same cryptographic primitives but would still need to recreate the consented legal and product constructs around compliant issuance. So while technical displacement is possible, practical displacement requires copying legal-operational work as well as code.
Still, assume a hypothetical competitor: Chain X releases a proof system that produces verifier computations 10x smaller and proving times 5x faster, plus a plug-and-play compliance module that regulators accept in pilot programs. Would Chain X instantly take DUSK’s customers? No — but Chain X would remove one of DUSK’s core technical differentiators: cost and execution efficiency for confidential business logic. If Chain X can also assemble a few well-placed partnerships and offer a migration plan that preserves asset continuity, DUSK could be pressured to respond quickly or risk being the “clunky” incumbent. The way DUSK hedges this risk is twofold: maintain modular ZK plumbing to swap proof backends and prioritize developer and partner tools that make migration costly for counterparties. Public documentation suggests DUSK is aware of the need to evolve the ZK stack, but continuous investment is required.
Security and attack surface deserve their own paragraph. Privacy increases the value of stolen metadata and off-chain correlatable data. For an institutional chain, the most damaging attacks are not necessarily classic double spends but targeted de-anonymization exploits, protocol bugs that allow unauthorized selective disclosures, or supply-chain weaknesses in third-party bridging and oracles. DUSK’s integration with Chainlink for data and CCIP for interoperability is smart from a reliability standpoint but also introduces dependency risk: an issue in cross-chain bridges or oracles can be exploited to replay, front-run, or leak regulated data. Defending against these threats requires hardened bridges, robust economic slashing for misbehaving nodes, verifiable on-demand audit proofs, and strong operational security across custodians. DUSK’s public materials claim attention to these components, but the real measure of defensibility will be how many independent security audits, red team exercises, and live stress tests they run against end-to-end product flows.
Governance and regulatory risk are often underestimated. Building institutional rails is not only a technical problem; it’s also a political one. DUSK’s NPEX deal indicates traction in regulated Europe, and that can be a double-edged sword: local regulatory approval helps adoption there but might complicate global scaling if different jurisdictions impose divergent rules on privacy features. To remain defensible, DUSK must support configurable disclosure policies and compliance templates that meet multiple legal regimes without fragmenting network utility. If DUSK becomes too tailored to one regulatory model, it risks becoming regionally locked. Conversely, if it remains too generic, institutions will worry about compliance precision. The technical solution is fine-grained, auditable disclosure; the business solution is a repertoire of legal-tech playbooks that the DUSK ecosystem can reuse. The partnership playbook with NPEX is a strong start, but scaling that approach to multiple markets requires sustained legal engineering.
Developer ecosystem and composability matter for long-term viability. EVM compatibility and integration with common tooling dramatically lower the cost for developers to build compliant dApps on DUSK. That said, EVM compatibility is necessary but not sufficient for a thriving ecosystem; developer experience for private smart contracts (debugging, testing, gas-profiling under ZK constraints) must be mature. DUSK’s teams have published resources and promoted DuskEVM, but the long tail of developers will adopt only if the toolchain reduces friction to the point where building private, compliant dApps becomes routine rather than arcane. Here the defensibility is a function of both engineering (tooling, SDKs, testnets) and commercial incentives (grants, incubators, exchange support). DUSK currently shows momentum in both directions.
Let’s return to the central binary: “one zk-upgrade away” implies an existential threat from a single technical breakthrough available to any chain. In raw cryptographic terms, breakthroughs can upset cost and expressivity assumptions. But two realities blunt that fear. First, institutional adoption is path-dependent; migrating live securities and workflows is operationally costly, legally entangled, and reputationally risky. Second, the most likely attackers in this space aren’t anonymous coders; they are well-funded competitors and incumbents who must also assemble partner ecosystems. To displace DUSK, a competitor must offer not just better ZK math but a ready-made, compliant migration pathway and demonstrable operational reliability. That’s a taller order than a single paper announcing a faster proof system. In short: a zk-upgrade can remove a technical advantage quickly, but it cannot instantly dissolve institutional moats and legal contracts.
What should DUSK do, given these realities, to make its defensibility real and durable? First, treat ZK modularity as a first-class architectural commitment: publish a clear upgrade path, open tool abstractions for pluggable proving backends, and fund ongoing integrations with emerging proof families via bounties and grants. Second, harden operational security and redundancy for bridges and oracles; run public, adversarial audits of the full RWA flow (issuance → custody → settlement → cross-chain transfer). Third, productize compliance: ship legally codified templates, auditor SDKs, and dispute-resolution primitives that reduce the cost of on-ramps for regulated firms. Fourth, scale partnerships beyond Europe: replicate the NPEX playbook with other licensed exchanges and custodians to convert technical wins into geographic and legal stickiness. Several of these moves are visible in public announcements — DUSK has been signing partners and integrating Chainlink — but execution pace matters.
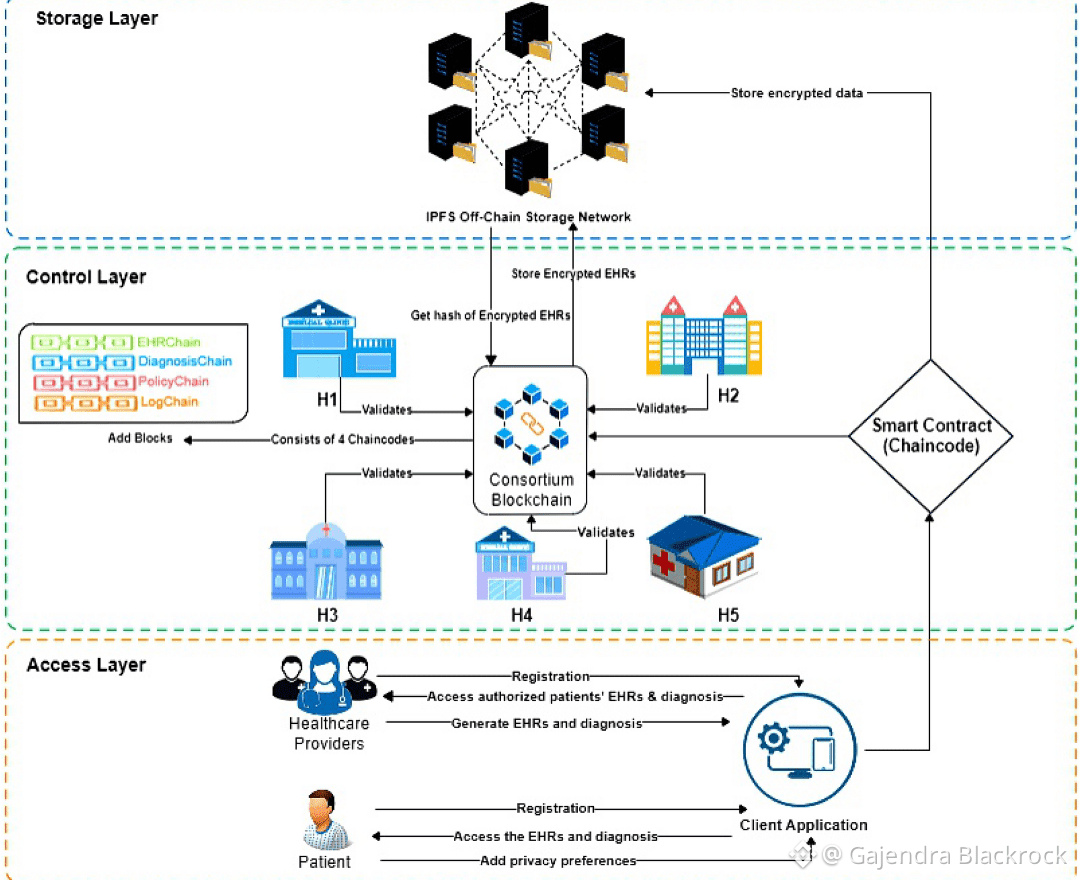
Finally, an honest read on competitive urgency: if you are an institutional counterparty evaluating DUSK today, the choice is between a near-term path that offers concrete compliant features and a speculative bet on a future chain with superior ZK math. If your priority is bringing regulated assets onchain now, DUSK is a defensible and pragmatic choice. If your priority is minimizing execution cost regardless of the time it takes to build governance and legal frameworks, you might prefer to wait for the next generation of ZK rails. For DUSK the imperative is to keep reducing migration friction and proving that live issuance flows remain cost-effective compared with the theoretical alternatives. The market for onchain RWAs values operational confidence over bleeding-edge crypto novelty; that grants DUSK breathing room — but not permanent immunity.
In summary: DUSK’s defensibility is real but conditional. The project has converted cryptographic ideas into institutional partnerships and product artifacts, which raises the bar for purely technical challengers. However, the underlying ZK landscape evolves rapidly, and a modular, upgradeable stack is required to avoid technical obsolescence. The single fastest route to displacing DUSK would be a competitor that bundles superior ZK efficiency with ready-made legal and migration pathways. That’s a high bar, but not impossible. DUSK’s strategic moves — NPEX, Chainlink integrations, explicit compliance framing, and an updated whitepaper — are the right bets to convert technical capability into a durable business moat. Execution speed, continuous ZK R&D, and rigorous security testing will determine whether DUSK remains defensible or becomes the incumbent struggling to adapt.
