The Mystery of Four Million Lost Bitcoins and the Concept of Digital Graves
The modern financial ecosystem is accustomed to operating within the rigid categories of assets and liabilities. However, deep within the heart of the Bitcoin blockchain, a third, hidden category exists: "digital dust." According to data from major blockchain analytics firms like Chainalysis and Glassnode, approximately four million Bitcoins are permanently locked in wallets that have shown no activity since the early era of cryptocurrency, specifically between 2009 and 2015. At current market valuations, this represents an astronomical sum exceeding one hundred and forty billion dollars. This is a capital reserve comparable to the annual gross domestic product of entire nations, yet it remains effectively removed from the global economy.

These funds have not vanished from the distributed ledger. They continue to exist as mathematical entries, becoming a form of "digital petroleum" that cannot be extracted using conventional methods. The problem of lost access to early-era assets has given birth to a specialized field within cryptography known as digital archaeology. The BitResurrector project, which has been updated to its most advanced version in early 2026, represents a technological response to this challenge. It provides a sophisticated instrument for the systematic reconstruction of lost private keys, shifting the paradigm from hopeless loss to scientific recovery.

Mathematical Fatalism Versus Technological Inevitability
The security of the Bitcoin protocol is built upon an assumption made by Satoshi Nakamoto regarding the immensity of the void. The search space for private keys is two to the power of two hundred and fifty-six, which is a number consisting of seventy-seven decimal digits. Official cryptographic doctrine states that finding a collision—where two independently generated keys correspond to the same address—is physically impossible within the lifetime of the universe. However, mathematics is a science of probability as much as it is a science of static constants.
The principle of random equality, which is embedded into the core architecture of BitResurrector, suggests that a point on the secp256k1 elliptic curve chosen by a pioneer in 2011 is not inherently different from a point generated by a computer today. Cryptography does not possess a memory of ownership, nor does it have an exclusive section for the elite. Any sequence of numbers created once can, by definition, be reproduced again. The real question is not whether it can happen, but rather the density of computations and the level of algorithmic optimization applied to the search. We are witnessing a period where the "infinite" void promised by the network's creator is gradually being shortened by the relentless pressure of Moore's Law and the increasing sophistication of software algorithms.

BitResurrector Engine Architecture: The Sniper Engine and the I/O Bottleneck
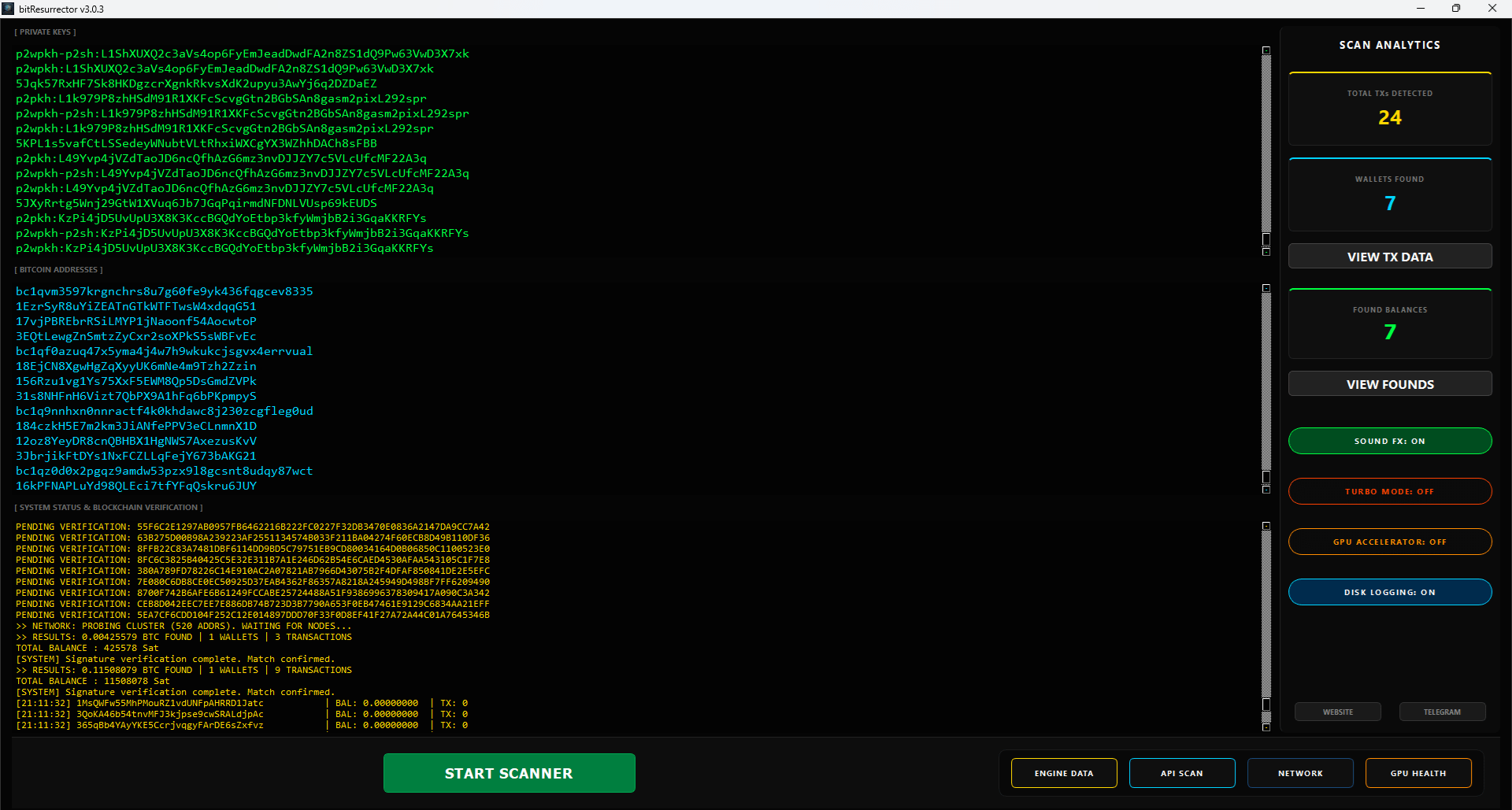
The primary obstacle for any software designed to search for cryptographic keys is the input-output bottleneck. Traditional methods of verifying a newly generated address against a database of active balances often rely on slow queries to hard drives or even high-speed solid-state drives. These delays, however small on an individual basis, become catastrophic when scaled to millions of checks per second. BitResurrector solves this fundamental challenge through the integration of Bloom Filter technology.

A Bloom Filter is a probabilistic data structure that allows the system to pack information regarding fifty-eight million active Bitcoin addresses—specifically those holding balances above one thousand satoshis—into a compact binary cache of approximately three hundred megabytes. In the Sniper Engine mode, the verification of a generated key against this global map occurs in constant time, or O(1), directly within the computer's random-access memory. This means the system does not waste a single microsecond waiting for a response from a storage device or a network request. The search speed increases by several thousand times, transforming a standard home computer into an autonomous computing node that rivals the performance of massive mining farms from the previous decade. The technical implementation within the current version also includes a hot-swap mechanism, which allows the program to rebuild its index in the background and perform an atomic pointer swap without interrupting the calculation process for even a fraction of a second.
Hardware Optimization: C++ Performance and AVX-512 Vectorization
The technical core of BitResurrector is written in high-performance C++ and utilizes specific hardware-level instructions. The latest versions implement support for AVX-512, which are advanced vector instructions that allow the processor to handle data packets of five hundred and twelve bits. Through a technique known as bit-slicing, a single processor core cycle can calculate up to sixteen independent private keys simultaneously.
Another significant innovation is the implementation of the Montgomery Modular Multiplication algorithm. In traditional cryptographic libraries, the modulo division operation is one of the most expensive tasks in terms of resource consumption, often requiring up to one hundred and twenty processor cycles. The Montgomery method replaces this division with fast bit shifts and additions, effectively freeing up more than eighty-five percent of the computational cycles that were previously spent waiting for the hardware to complete the operation. This is a form of technological acceleration that allows the equipment to work at its physical limit without generating unnecessary heat. The application of the REDC formula ensures that your processor starts doing the work that would normally require ten similar processors running less optimized code.
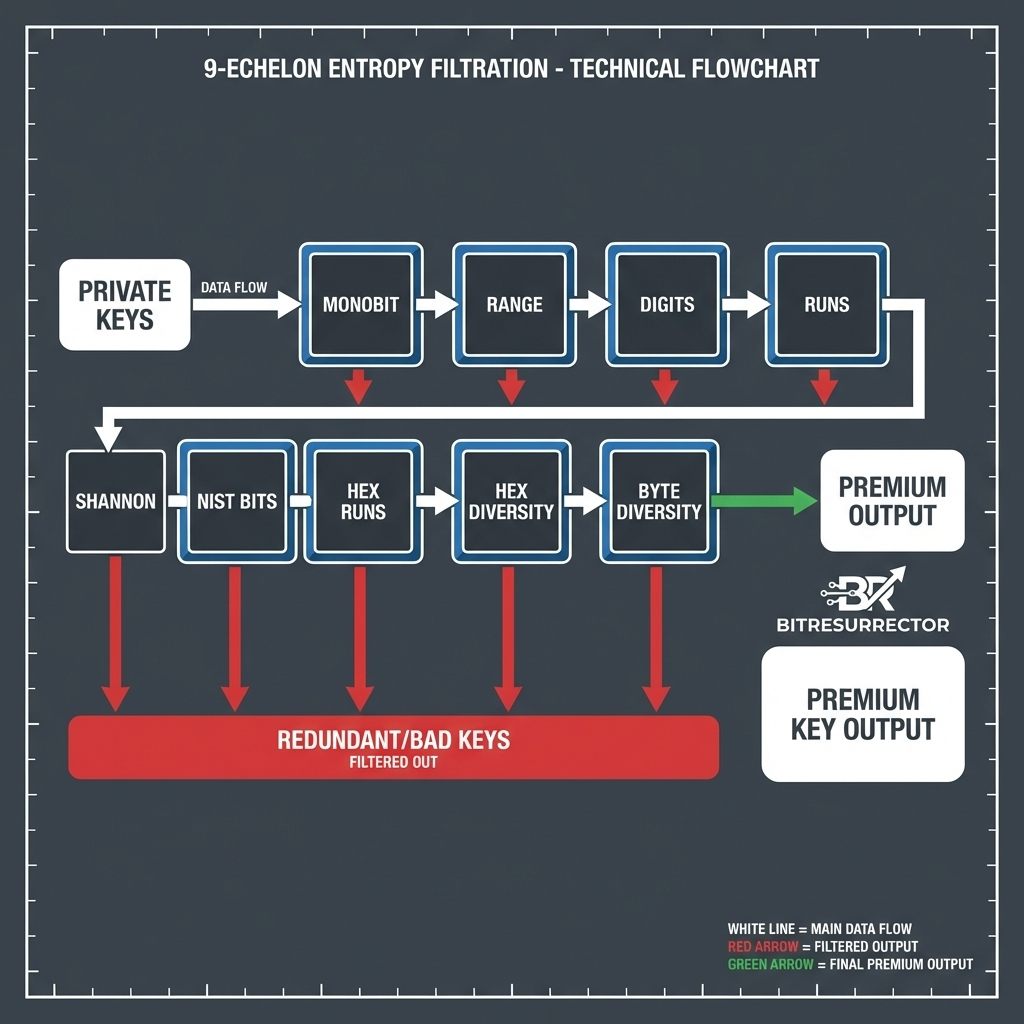
Intelligent Entropy Filtration: The Nine Echelons of Cryptanalysis
BitResurrector does not merely generate random numbers in a vacuum. Instead, it functions as a high-precision separator. A major problem with early Bitcoin wallets developed between 2010 and 2014 was that their random number generation algorithms often suffered from mathematical flaws. Many early mobile wallets and web services used insufficient sources of entropy, leading to the creation of keys with predictable patterns.
The filtration system within BitResurrector subjects every generated scalar to a rigorous analysis across nine independent echelons, ensuring that computational resources are only invested in sequences that show true cryptographic strength. This process is far more efficient than simple brute force.
The first echelon involves a frequency analysis of binary density, known as the NIST Monobit Test. This barrier performs a Hamming weight evaluation for every two hundred and fifty-six-bit scalar. In a perfectly random key, the number of "ones" and "zeros" should follow a binomial distribution. If the number of set bits falls outside the trusted range, the key is recognized as a defective product of entropy starvation and is discarded.
The second echelon focuses the system's power on the region of maximum information density. The algorithm restricts its search to a specific range of seventy-seven decimal digits. This segment covers approximately seventy-eight percent of the theoretical scalar field and excludes low-complexity passphrases and short keys that were never used by professional-grade wallets like Electrum or Bitcoin Core.
The third echelon checks for the combinatorial diversity of the decimal alphabet. A key is only recognized as valid if its decimal representation contains nine or more unique digits out of ten. The probability of a truly random key having fewer than nine unique digits is vanishingly small. This threshold allows the program to instantly identify keys generated by primitive algorithms with short repetition periods.
The fourth echelon utilizes Shannon entropy metrics to measure the unpredictability of the key. Named after the father of information theory, Claude Shannon, this metric ensures that only "true chaos" passes into the verification loop. If a key shows any signs of information collapse or structural "garbage," it is either discarded or prioritized for deeper investigation via external blockchain APIs, as such low-entropy keys are often a direct indicator of specific vulnerabilities found in early wallet software.
The fifth and sixth echelons perform serial analysis and longest run tests. They search for anomalous repetitions of digits or bits. For instance, the appearance of a long-chain like seven identical zeros in a row is a fatal marker of deterministic behavior that has no place in a cryptographic search pipeline. Similarly, binary runs of seventeen or more identical bits are flagged as as sequential entropy collapse, often caused by hardware failures in random number generators.
The final three echelons focus on hexadecimal cyclicity, spectral diversity of nibbles, and byte-level sparsity. These checks ensure that the key does not contain memory alignment artifacts or initialization patterns that would make it vulnerable to specific cryptographic attacks. This multi-layered approach ensures that every processor cycle is used effectively, turning a chaotic search into an organized scientific operation.
Operating Modes: Sniper Versus API Global Navigation
BitResurrector offers two primary strategic paths depending on the user's priorities: sheer speed or absolute verification accuracy. The Sniper mode is the pinnacle of autonomy and raw performance. It is designed for high-velocity offline scanning of an infinite key space. In this mode, the program avoids all network latency and third-party API limits. It relies entirely on the local Bloom Filter map to check millions of combinations per second.
In contrast, the API Global mode is designed for precision verification in real-time. While it is naturally slower due to the constraints of blockchain explorers, it provides a "live" view of the network. This mode can confirm balances on addresses that were created very recently or those that might have been missed in a daily database dump. By combining these two modes, a user can balance the gross coverage provided by the Sniper engine with the guaranteed relevance of the API Global module.
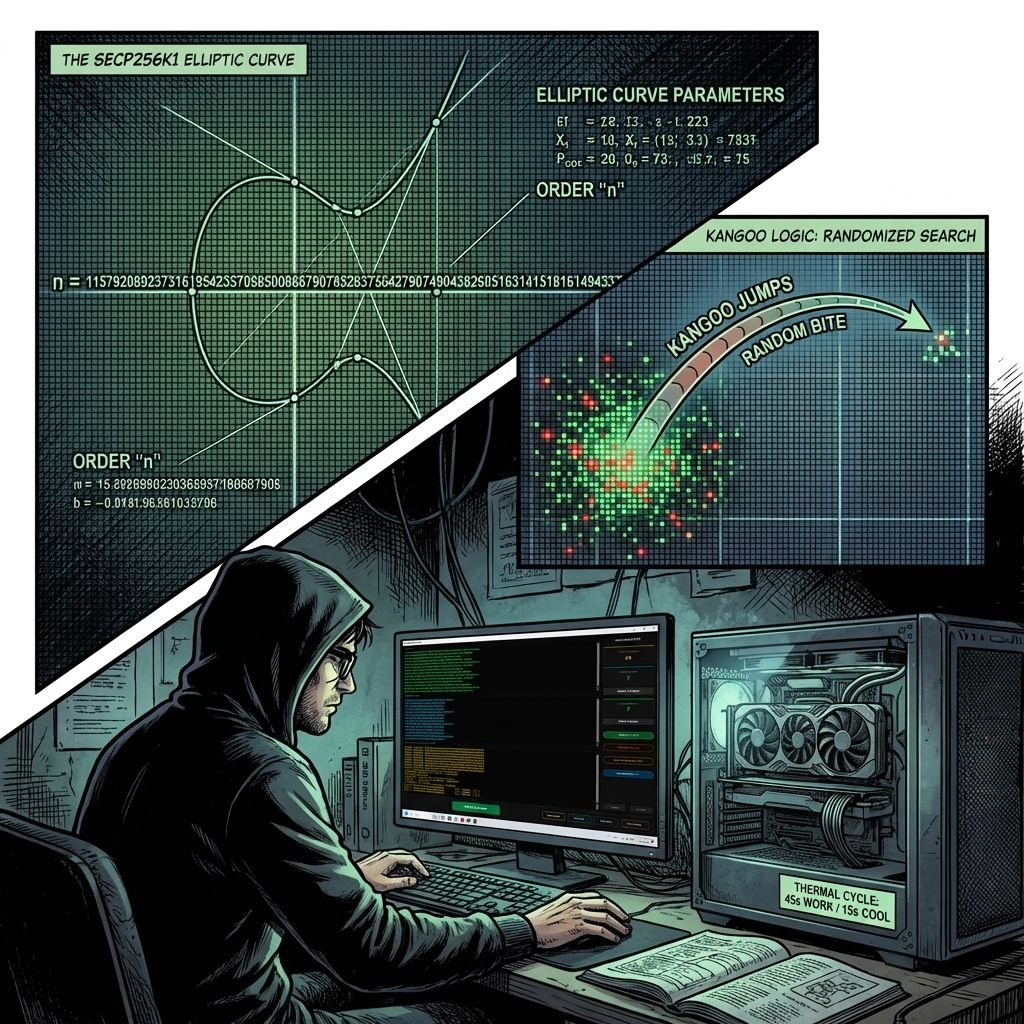
GPU Acceleration and the Stochastic Search Strategy
When dealing with trillions of combinations, the central processing unit eventually yields its dominance to the massive parallelism of graphics cards. By integrating the NVIDIA CUDA platform, BitResurrector transforms a modern GPU into an industrial-scale scanner. However, because the key space is so vast, a linear scan would be inefficient.
Instead, the program implements a stochastic search strategy known as "Random Bites" or "Kangoo Jumps." In this mode, the graphics card selects a random coordinate in the target range and initiates a deep "excavation" for forty-five seconds. If no match is found, the system makes an instant jump to an entirely new random area of the blockchain. This method exponentially increases the chances of discovering a collision because the search does not get stuck in "empty" sectors of the address space. Furthermore, to protect the longevity of expensive hardware, the software includes a thermal duty cycle system that allows the video card to cool down between intense calculation phases.
The Phenomenon of Zombie Coins and Statistical Probability
Critics of digital archaeology often use astronomical numbers to claim that finding an early-era key is impossible. However, it is essential to look at the facts through the lens of logic rather than fear. When a "whale" created an address in 2011, their computer simply outputted a random number. That computer did not have a special version of mathematics or a blessing from a higher power. It was a single event in the same probability space that your computer occupies today.
The theory of probability has no memory. You are not required to search through trillions of "bad" keys before finding a "good" one. Every second that BitResurrector runs is an independent roll of the dice. The difference between a zero percent chance and a nearly zero percent chance is the exactly the crack in the door that this software seeks to exploit. In a world where one hundred and forty billion dollars are at stake, the fact that a collision is mathematically possible is more than enough reason for practitioners of digital archaeology to continue their work.
Ethical Perspectives and the Mission of Free Distribution
At first glance, the free distribution of such powerful software might seem paradoxical. Why would developers share an instrument capable of discovering dormant billions? The answer lies in the fundamental principles of decentralization and financial justice. First, the project believes that access to "treasure hunting" technologies should not be a privilege for a small elite who can afford supercomputer rentals. By providing the software for free, we give every person with a computer a chance to change their financial status.
Second, the resurrection of abandoned coins serves the health of the entire Bitcoin ecosystem. Millions of Bitcoins resting as dead weight create an artificial deficit and reduce market liquidity. By returning these funds to active circulation, users of the software act as "resuscitators" for the network. Every successful recovery makes Bitcoin a more vibrant and functional financial instrument for the global community. Finally, BitResurrector serves as a large-scale technological audit. It signals to the world that current security standards are not absolute and that the time has come to develop truly quantum-resistant and secure systems for the future.
Security Context and the Fear of Professional Code
Users often encounter warnings from antivirus software and system protection tools when installing BitResurrector. These are typically "false positives" caused by the nature of the code itself. Professional cryptographic software uses direct memory access, optimized assembly insertions, and high-intensity GPU usage—all of which are behaviors that antivirus heuristic engines often associate with malicious software like miners or ransomware.
The program has passed numerous checks on platforms like VirusTotal and is recognized as legitimate within the community of "white hat" researchers. The warnings are simply a side effect of modern operating systems being designed for sterilized, low-performance applications rather than high-intensity mathematical research tools. Adding the program folder to the exclusions list of your security software is a standard procedure for anyone working with industrial-grade cryptographic tools.
Conclusion: Choosing Between BitResurrector and AI Seed Finder
BitResurrector version 3.0 is a powerful instrument for "at-home" digital archaeology. It is ideal for those who have spare hardware and the patience to engage in a long-term search. It is transparent, honest, and offers a genuine chance at a life-changing discovery while your computer is otherwise idle. Every day that the program runs brings you closer to a mathematical collision that could solve all your material needs.
However, it is vital to maintain a realistic perspective. A home computer is a narrow window into the infinity of numbers. For those who seek a more industrial approach with a focus on guaranteed results rather than sheer luck, there is a more advanced project known as the AI Seed Phrase Finder. While BitResurrector is like a personal fishing rod, the AI Seed Phrase Finder is like an industrial trawler equipped with artificial intelligence radar. The latter offloads heavy computations to remote server clusters and uses neural networks to predict the most probable areas of the blockchain to find active wallets, narrowing the search space by millions of times.
The choice depends on your resources and your goals. If you have an interest in the technology and a desire to participate in a free, decentralized hunt, BitResurrector is your best ally. If you are aimed at rapid and professional asset reconstruction, the AI Seed Phrase Finder is the logical next step. In either case, the age of digital archaeology has arrived, and for the first time in history, the power of modern silicon gives every individual a chance to challenge the silence of the blockchain and reclaim the lost treasures of the digital past.
Frequently Asked Questions
Which graphics cards are recommended for the best results?
The system is optimized for NVIDIA cards from the 30-series and 40-series due to their high density of CUDA cores. The more cores available and the faster the video memory, the more combinations can be checked every second.
Does the software require a constant internet connection?
No, the Sniper engine is designed to work entirely offline. An internet connection is only necessary for the initial setup and periodic updates to the Bloom Filter database, which typically occur once per day to ensure the map of active addresses remains current.
Is there a risk of damaging the hardware during the search?
The Turbo Core mode is designed to manage processor load intelligently. However, because the software utilizes advanced vector instructions like AVX-512, it is recommended to have a high-quality cooling system in place. The GPU thermal duty cycle also helps to prevent overheating during intense calculation phases.

How can I be sure the software is safe to use?
Always ensure that you are downloading the program from the official GitHub repository. The software has a long history of use by thousands of researchers worldwide and consistently passes security scans on platforms like VirusTotal.
The intersection of mathematics, probability, and high-performance computing has created a unique window of opportunity. Whether you are a technologist interested in the limits of cryptography or someone seeking financial sovereignty, the tools for digital archaeology are now within your reach. Patience, hardware, and the laws of probability are the only things standing between you and the dormant treasures of the Bitcoin network.
For those interested in exploring these technologies further and staying updated on the latest developments in digital archaeology, more information can be found at the obzoroff.info/bitresurrector. Additionally, the BitResurrector software and its associated community resources are easily accessible by simply entering the project name bitResurrector into any major search engine. Using a direct search for the project name is the most reliable way to locate the current official distribution and technical documentation without relying on external links.
