Everyone assumes that if data exists on-chain, it's safe. Wrong. Walrus proves the real security comes after retrieval: re-encoding the blob you read and verifying it matches the on-chain commitment. This simple mechanism is what makes decentralized storage actually trustworthy.
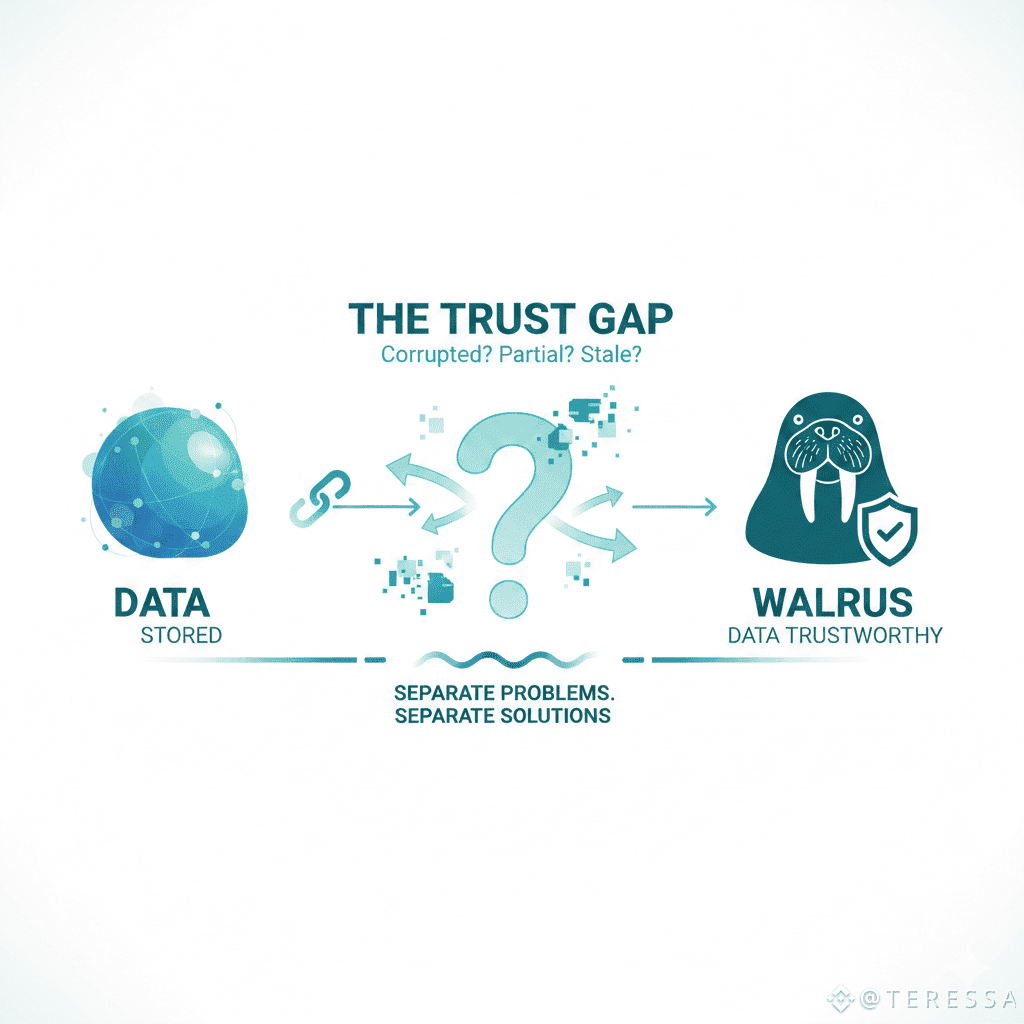
The Trust Gap Nobody Addresses
Here's what most storage systems pretend: once your blob is on-chain, you can trust any validator's claim about having it. That's security theater.
A validator can serve you corrupted data and claim it's authentic. They can serve partial data claiming it's complete. They can serve stale data from months ago claiming it's current. Without verification, you have no way to know you're getting legitimate data.
This is the gap between "data is stored" and "data is trustworthy." Most systems conflate them. Walrus treats them as separate problems that need separate solutions.
On-chain commitment proves data was stored. Read + re-encode proves what you retrieved is legitimate.
The Read + Re-encode Protocol
Here's how Walrus verification actually works:
You request a blob from the network. Validators serve you slivers. You retrieve enough slivers to reconstruct the blob. Then—this is critical—you re-encode the reconstructed blob using the same erasure code scheme.
The re-encoded result produces a new set of commitments. You compare these to the original on-chain commitment. If they match, the blob is authentic. If they don't, it's corrupted, modified, or you've been served fake data.
This single check proves:
The data is complete (you reconstructed it)
The data is genuine (commitments match)
The data is current (commitments are version-specific)
Validators didn't lie (evidence is cryptographic)
Why This Works Better Than Other Approaches
Traditional verification approaches rely on spot-checking. Query multiple validators, assume the majority is honest, accept their consensus. This is probabilistic and vulnerable to coordinated attacks.
Walrus verification is deterministic. One re-encoding tells you everything. Validators can't manipulate consensus because there's no voting. The math either works or it doesn't.
Cryptographic proof beats democratic voting every time.
The Bandwidth Math of Trust
Here's what makes this elegant: re-encoding costs O(|blob|) bandwidth—you have to receive the entire blob anyway to trust it. There's no additional verification overhead beyond retrieval.
Compare this to systems that do multi-round verification, quorum checks, or gossip-based consensus. Those add bandwidth on top of retrieval.
Walrus verification is "free" in the sense that the bandwidth is already being used. You're just using it smarter—to verify while you retrieve.
Commitment Schemes Matter
Walrus uses specific erasure coding schemes where commitments have beautiful properties. When you re-encode, the resulting commitments are deterministic and unique to that exact blob.
This means:
Validators can't craft fake data that re-encodes to the same commitments (infeasible)
Even a single bit change makes commitments completely different (deterministic)
You can verify without trusting who gave you the data (mathematical guarantee)
The commitment scheme itself is your security, not the validators.
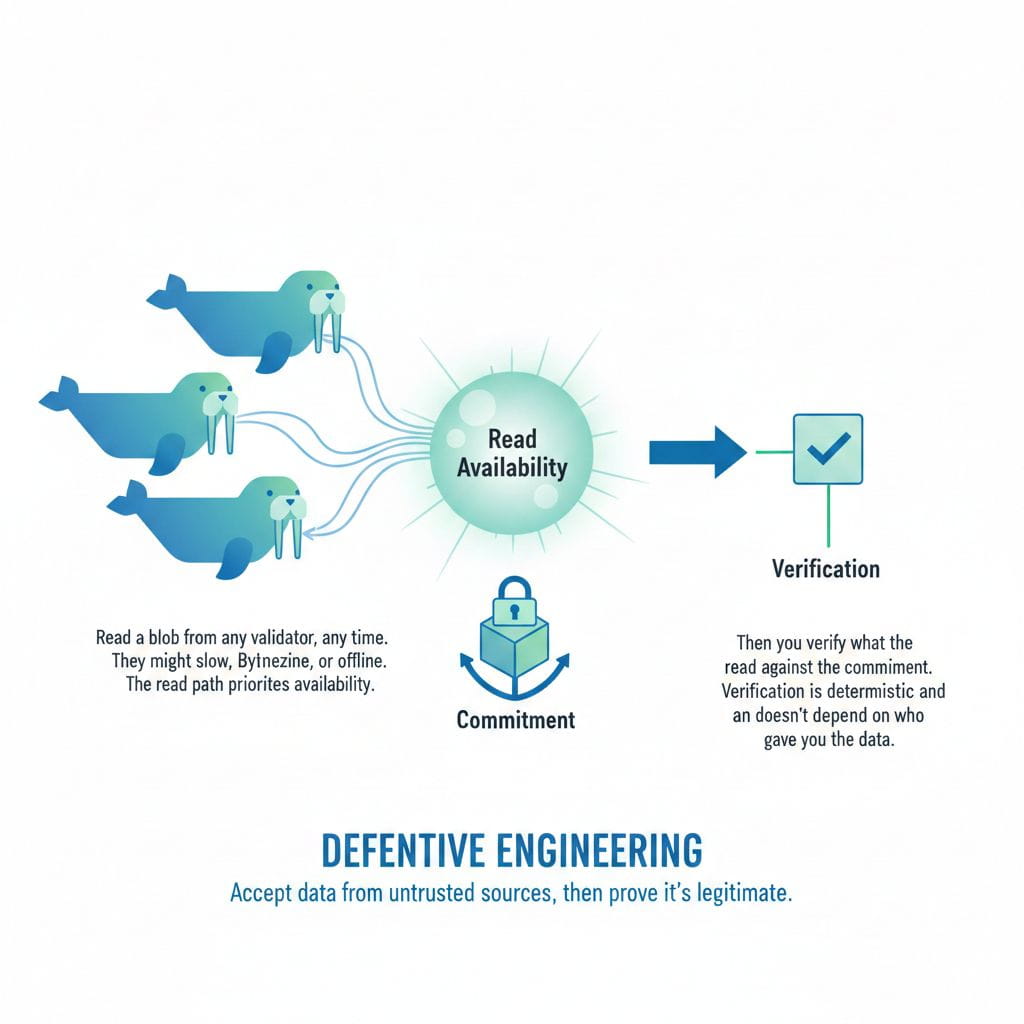
Read Availability vs Verification
Here's where design maturity shows: Walrus separates read availability from verification.
You can read a blob from any validator, any time. They might be slow, Byzantine, or offline. The read path prioritizes availability.
Then you verify what you read against the commitment. Verification is deterministic and doesn't depend on who gave you the data.
This is defensive engineering. You accept data from untrusted sources, then prove it's legitimate.
What Verification Protects Against
Re-encoding verification catches:
Corruption (accidental or deliberate)
Data modification (changing even one byte fails verification)
Incomplete retrieval (missing data fails commitment check)
Validator dishonesty (can't produce fake commitments)
Sybil attacks (all attackers must produce mathematically consistent data)
It doesn't catch everything—validators can refuse service. But that's visible. You know they're being unhelpful. You don't have the illusion of trusting them.
Partial Blob Verification
Here's an elegant detail: you can verify partial blobs before you have everything. As slivers arrive, you can incrementally verify that they're consistent with the commitment.
This means you can start using a blob before retrieval completes, knowing that what you have so far is authentic.
For applications streaming large blobs, this is transformative. You don't wait for full retrieval. You consume as data arrives, with cryptographic guarantees that each piece is genuine.
The On-Chain Commitment as Ground Truth
The on-chain commitment is the single source of truth. Everything else—validator claims, network gossip, your initial read—is suspect until verified against the commitment.
This inverts the trust model. Normally you trust validators and assume they're protecting the commitment. Walrus assumes they're all liars and uses the commitment to detect lies.
The commitment is small (constant size), verifiable (mathematically), and permanent (on-chain). Everything else is ephemeral until proven against it.
Comparison to Traditional Verification
Traditional approach: trust validators, spot-check consistency, hope the quorum is honest.
Walrus approach: trust no one, re-encode everything, verify against commitment cryptographically.
The difference is categorical.
Practical Verification Cost
Re-encoding a 100MB blob takes milliseconds on modern hardware. The bandwidth to receive it is already budgeted. The verification is deterministic and fast.
Verification overhead: negligible in terms of time and bandwidth. Gain: complete certainty of data authenticity.
This is why verification becomes practical instead of theoretical.
The Psychology of Trustlessness
There's something powerful about systems that don't ask you to trust. "Here's your data, here's proof it's legitimate, verify it yourself." This shifts your relationship with infrastructure.
You're not relying on validator reputation or team promises. You're relying on math. You can verify independently. No permission needed.
@Walrus 🦭/acc Read + Re-encode represents maturity in decentralized storage verification. You retrieve data from untrusted sources, re-encode to verify authenticity, match against on-chain commitments. No quorum voting. No probabilistic assumptions. No trusting validators. Just math proving your data is genuine.
For applications that can't afford to trust infrastructure, that can't compromise on data integrity, that need cryptographic certainty—this is foundational. Walrus gives you that guarantee through elegant, efficient verification. Everyone else asks you to believe. Walrus lets you verify.


