
You can lose everything while your phone sleeps in your pocket.
No alert.
No hacked password.
No “Approve” button clicked today.
Yet when you open your wallet…
your balance is zero.
This is not a rare edge case anymore.
This is one of the most common loss mechanisms in Web3—and almost nobody talks about it clearly.
You Don’t Need to Be Online to Get Drained
In traditional finance, theft usually requires access.
In crypto, it doesn’t.
If a malicious contract already has permission,
your wallet doesn’t need to be active at all.
The transaction happens on-chain.
Your funds move.
You find out later.
That’s the nightmare scenario.
The Real Attack Vector: Unlimited Approvals
Hackers are not guessing seed phrases.
They are not brute-forcing Ledger devices.
They are exploiting something much simpler:
Old signatures you forgot about
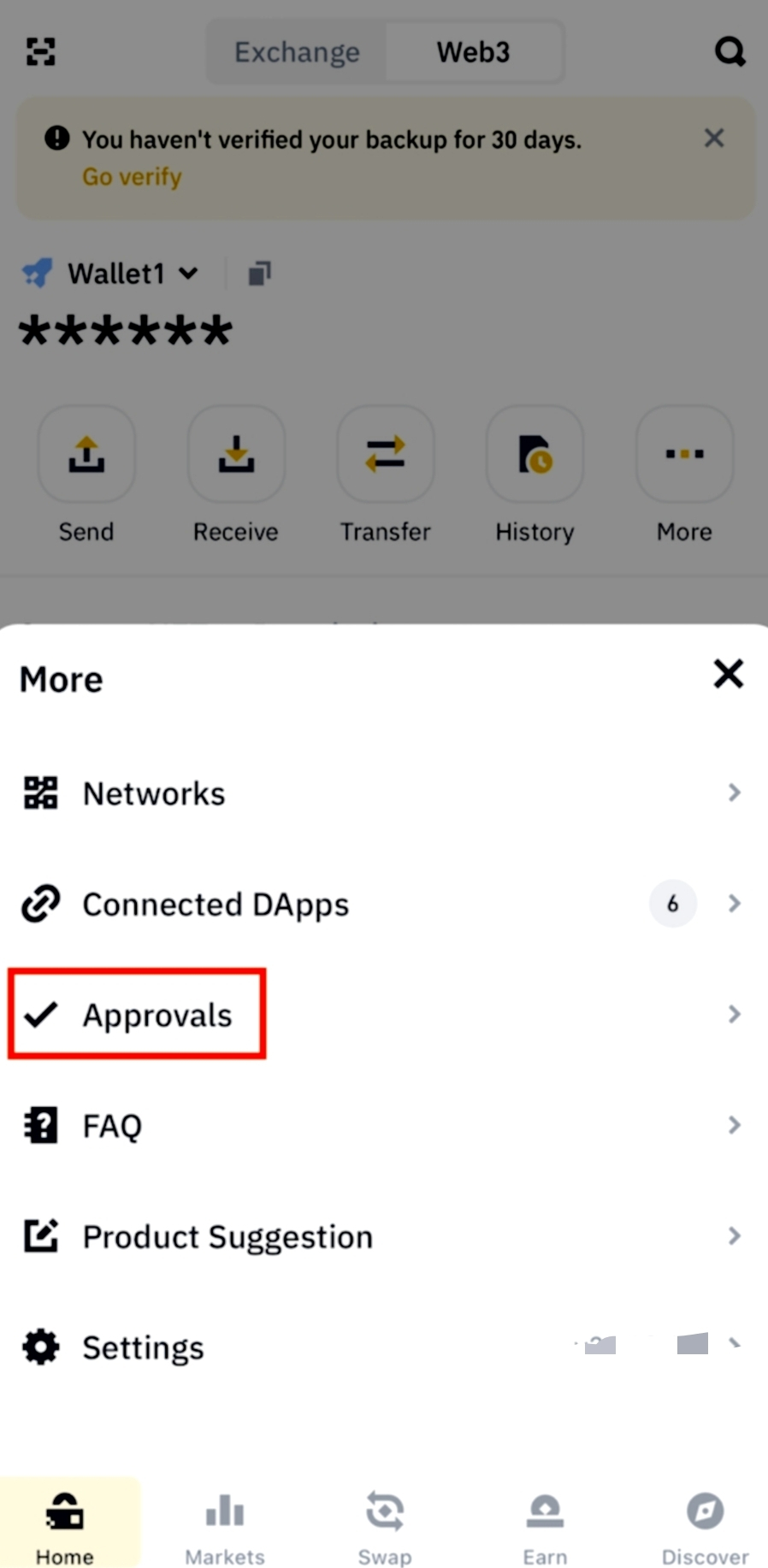
At some point, you probably:
Connected MetaMask to a dApp
Minted an NFT
Claimed an airdrop
Used a DeFi protocol once and never returned
During that interaction, you likely approved:
“Unlimited access to your tokens”
Not your wallet.
Your tokens.
Why This Is So Dangerous
Once approved, a smart contract can:
Transfer tokens anytime
Drain balances when they increase
Act without your presence
And here’s the scary part:
The approval does not expire.
It can sit there for months…even years.
Why Hackers Wait for Bull Markets
This isn’t random theft.
It’s patient extraction.
Attackers:
Monitor wallets silently
Track balances over time
Wait for bull markets, bonuses, new deposits
Then, when your portfolio finally looks healthy again—they empty it in one block.
No drama.
No warning.
“But I Use a Ledger” (The Biggest Myth)
This is where most people feel safe.
And where most people are wrong.

A hardware wallet:
Protects your private keys
Does not protect you from permissions you already granted
If you signed a malicious or overly broad contract:
Your Ledger will approve the transaction exactly as designed
Because the contract is doing what you allowed it to do.
Why ‘Connect Wallet’ Became the Most Dangerous Button in Web3
“Connect Wallet” feels harmless now.

It’s everywhere:
Binance Web3
NFT marketplaces
DeFi dashboards
Airdrop claim pages
But behind that button is a question most users never ask:
What permissions am I giving right now?
Blind trust is the real vulnerability.
Custody Is Not Enough
Self-custody is powerful.
But it’s incomplete without permission control.

True wallet security requires:
Key security
Device security
Approval management
If you don’t manage approvals,
you don’t fully control your wallet.
The Question That Actually Matters
Not:
“Is my wallet cold?”
But:
“Who still has access to my assets?”
Ask yourself honestly:
When was the last time you checked your approvals?
How many contracts can still move your funds?
Do you recognize all of them?
Most people don’t.
The Silent Rug Pull Nobody Sees
This isn’t a hack. This isn’t phishing. This isn’t user error today.
It’s delayed consequence.
Silence in crypto is not safety.
It’s often just time passing before execution.
How Smart Users Protect Themselves
Not by panic.
By discipline.
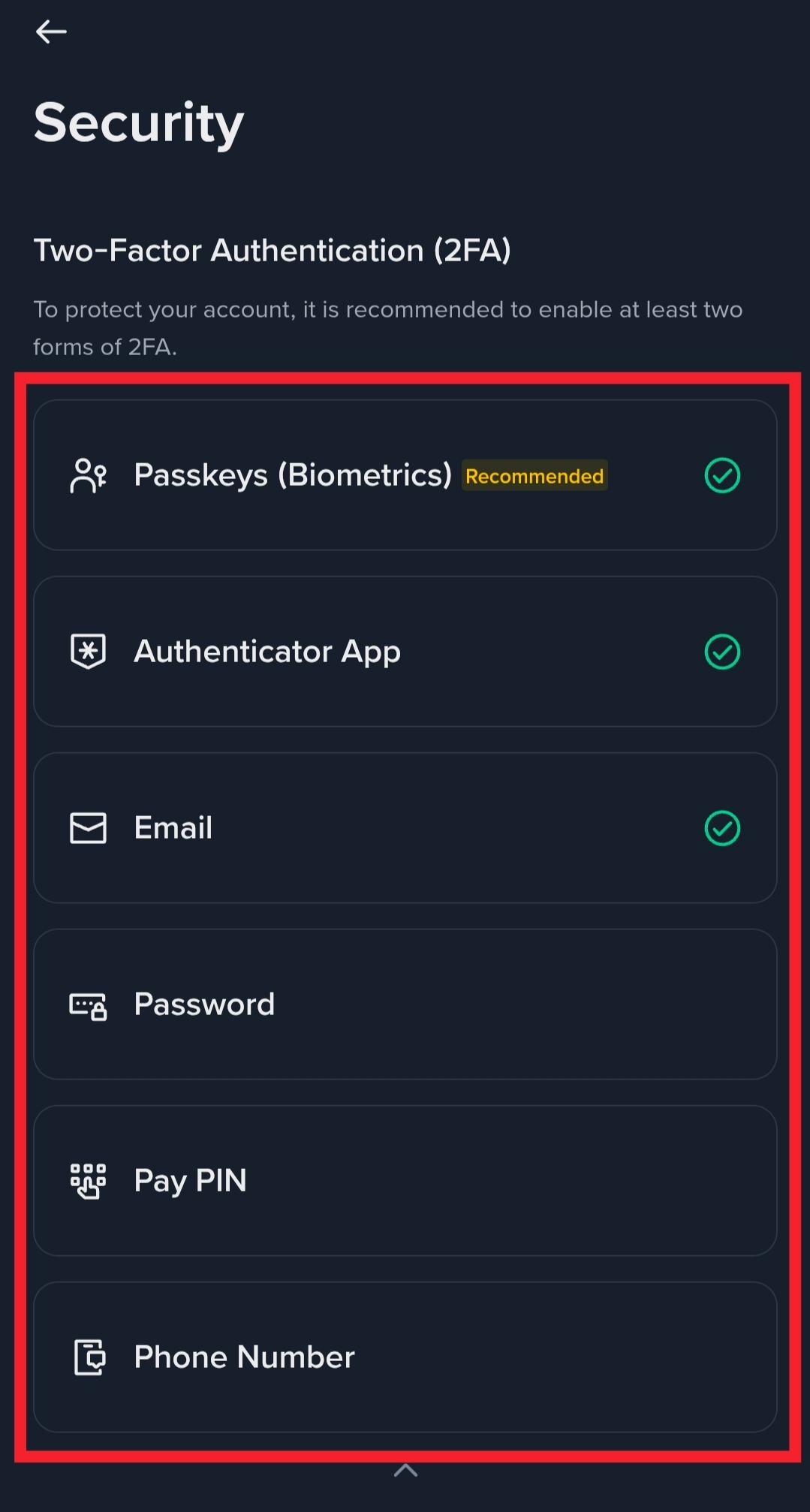
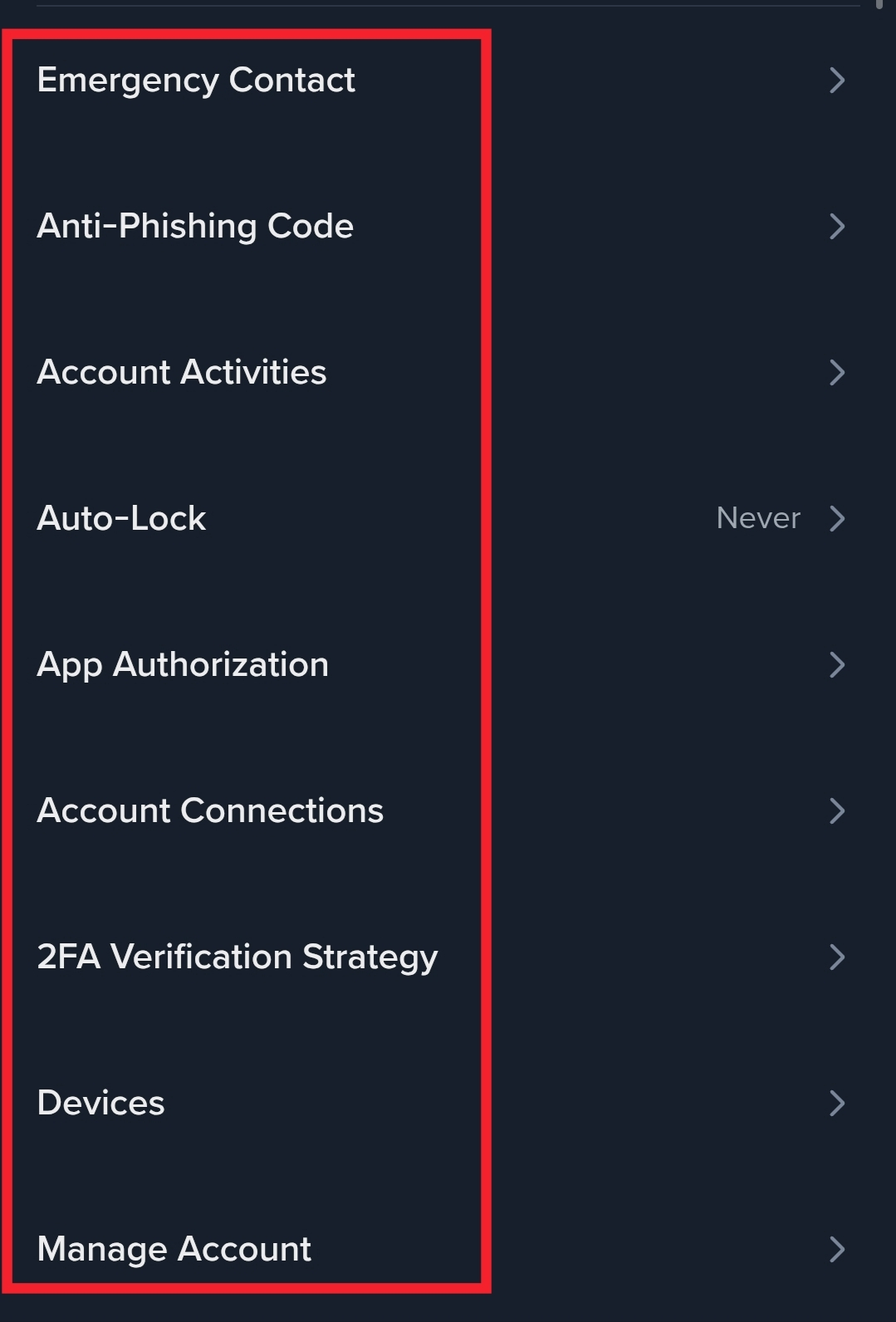
Smart users:
Review token approvals regularly
Revoke access they no longer need
Treat every signature like a financial contract
Never approve “unlimited” unless absolutely necessary
Security in Web3 is not about fear.
It’s about awareness.
Crypto doesn’t punish ignorance immediately.
It waits.
And when it acts, it does so perfectly, automatically, and without mercy.
If this made you uncomfortable, that’s good.
Discomfort is awareness forming.

If you learned something here:
Save this post
Share it with someone who uses MetaMask or Binance Web3
Check your approvals today
In crypto, the biggest risk isn’t volatility.
It’s forgotten permissions.


