Most crypto discussions still assume the same future: open ledgers, radical transparency, and permissionless everything. That worldview made sense when blockchains were experimental playgrounds. It makes far less sense once real financial institutions enter the picture.
Finance does not operate in public by default.
It operates through controlled disclosure.
This is where Dusk quietly separates itself from both general-purpose Layer 1s and “privacy-first” chains that misunderstand what regulation actually requires.
The Core Misalignment in Crypto Privacy
The majority of privacy-focused blockchains treat privacy as invisibility. Transactions are hidden, data is obscured, and the goal is to reveal as little as possible to anyone. That approach appeals to crypto-native users, but it immediately collapses under regulatory scrutiny.
Regulators don’t oppose privacy.
They oppose unverifiable systems.
In real markets, institutions must be able to prove correctness, compliance, and solvency — selectively, to authorized parties, under defined conditions. A system that hides everything equally from everyone is unusable in that context.
Dusk’s approach is different because it treats privacy as a system constraint, not a marketing feature.
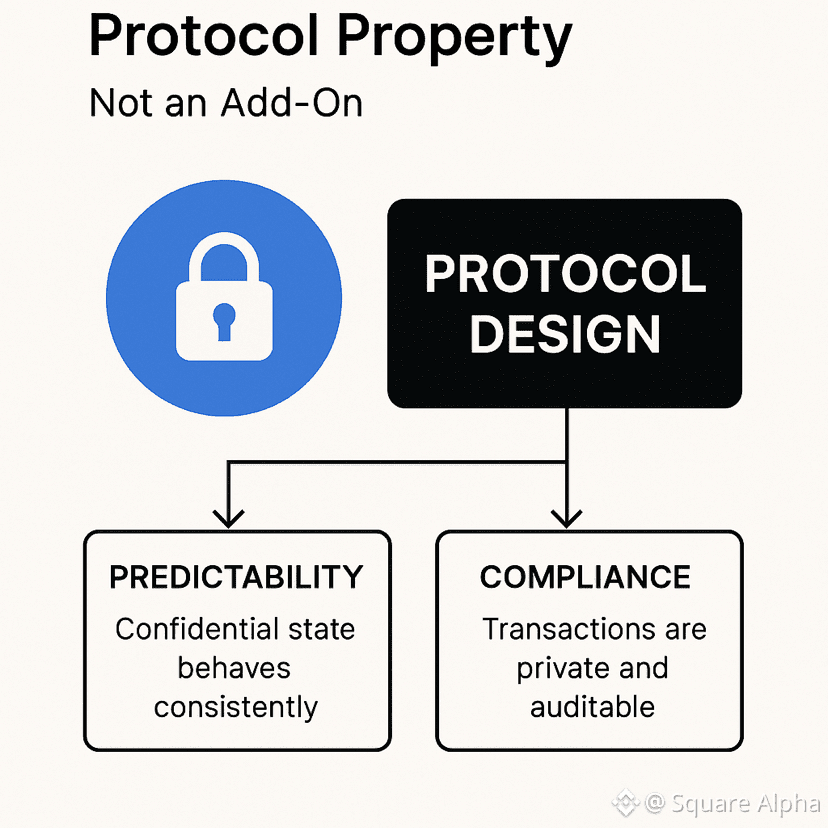
Privacy as a Protocol Property, Not an Add-On
Dusk embeds privacy directly into its protocol design. Confidentiality is not achieved through external mixers, optional overlays, or off-chain workarounds. Instead, privacy and auditability are handled at the execution and verification level.
This matters for two reasons.
First, it creates predictability. Developers know how confidential state behaves, how it’s verified, and how it interacts with consensus. There are no hidden assumptions or fragile integrations.
Second, it aligns with compliance realities. Transactions can remain confidential to the public while still being provable when required. That distinction — private by default, auditable by design — is where most blockchains fail.
This architecture becomes especially important as Dusk transitions from infrastructure to application deployment.
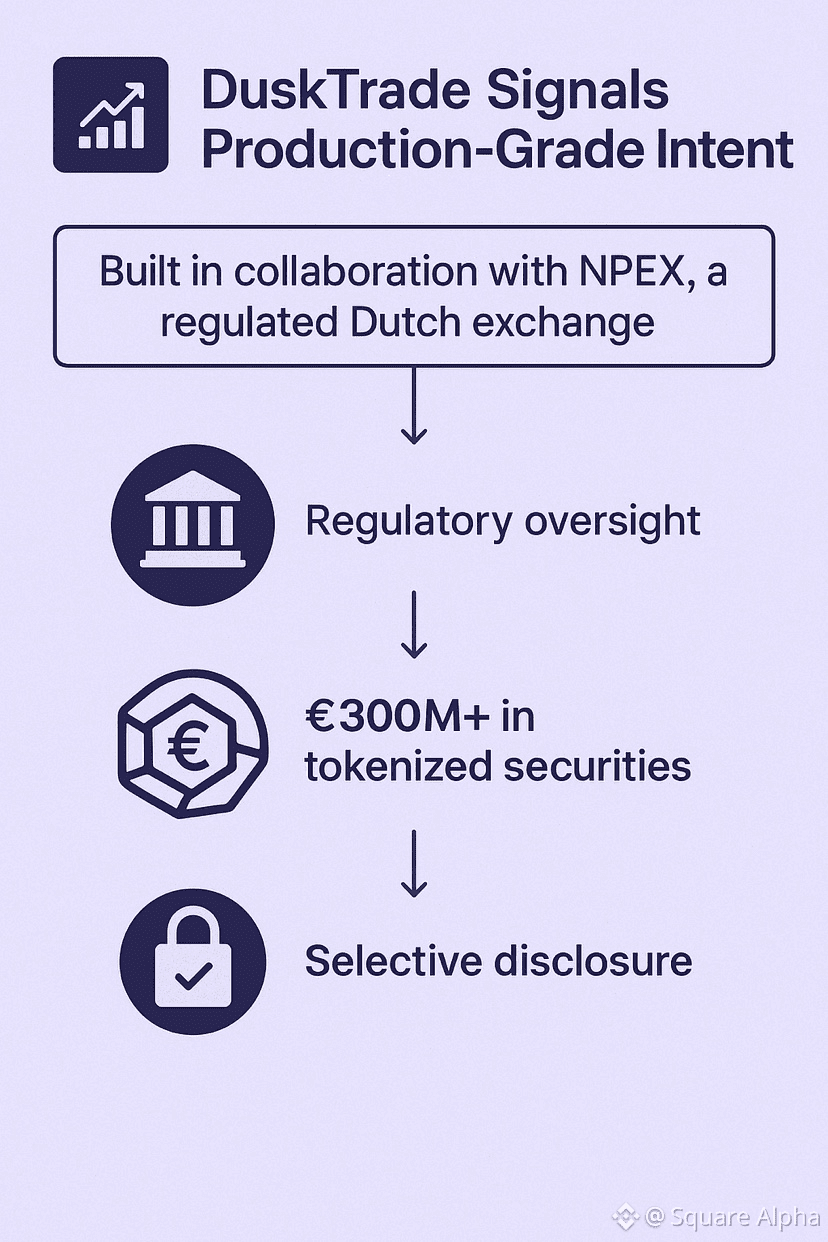
DuskTrade Signals Production-Grade Intent
The upcoming DuskTrade platform is not positioned as an experimental RWA showcase. It is being built in collaboration with NPEX, a regulated Dutch exchange holding MTF, Broker, and ECSP licenses.
That context changes everything.
Tokenizing securities is not just a technical challenge. It requires custody rules, reporting obligations, and regulatory oversight. A blockchain that cannot support selective disclosure at the protocol level simply cannot operate in this environment.
By targeting €300M+ in tokenized securities and opening a waitlist, Dusk is signaling readiness for real market interaction — not testnet demonstrations.
This is where Dusk’s privacy model becomes operational, not theoretical.
DuskEVM Lowers Friction Without Sacrificing Control
One of the smartest strategic decisions Dusk has made is launching DuskEVM as an EVM-compatible application layer that settles on Dusk’s Layer 1.
From an institutional perspective, familiarity reduces risk.
Solidity tooling, existing development workflows, and known execution models allow teams to deploy without re-engineering their entire stack. At the same time, settlement occurs on a Layer 1 explicitly designed for regulated financial use cases.
This combination is rare.
Most EVM chains prioritize composability and speed, then struggle to retrofit compliance later. Dusk flips that model: compliance and privacy are foundational, while EVM compatibility is added to unlock adoption.
Hedger: Where Privacy Becomes Usable
Hedger is where Dusk’s philosophy becomes concrete.
By enabling privacy-preserving yet auditable transactions on EVM using zero-knowledge proofs and homomorphic encryption, Hedger addresses the exact tension institutions face: how to protect sensitive data without creating opaque systems.
The fact that Hedger Alpha is live matters. It shows that privacy on Dusk is not a roadmap promise — it is already being implemented and tested within the execution environment.
This reinforces Dusk’s positioning as infrastructure built for controlled financial activity, not anonymous experimentation.
What This Means for DUSK
In this model, the $DUSK token is not driven by narratives or short-term hype cycles. Its relevance is tied to network usage: staking, transaction execution, and participation in compliant financial applications.
As DuskTrade, DuskEVM, and privacy-enabled execution move into production phases, demand becomes structural rather than speculative. That doesn’t guarantee rapid price movement — but it does align token value with actual system activity.
Final Perspective
Dusk is not trying to win crypto’s attention economy.
It is preparing for an environment where blockchain must coexist with regulation, reporting, and institutional accountability.
Privacy, in this context, is not about hiding.
It is about control.
By designing privacy as selective, auditable, and enforced at the protocol level, Dusk positions itself for a phase of adoption many networks are structurally unprepared for.
That may not generate loud narratives today — but it is exactly how real financial infrastructure gets built.
