According to on-chain investigator @ZachXBT , a victim lost over $282 million in $BTC and $LTC after falling for a sophisticated social-engineering attack targeting their hardware wallet. The attacker gained remote access, drained the funds, then immediately laundered portions by swapping $LTC/$BTC into $XMR (causing a sharp price spike) and routing 818 BTC (~$78M) through THORChain into 19,631 ETH, 3.15M XRP, and 77,285 LTC.
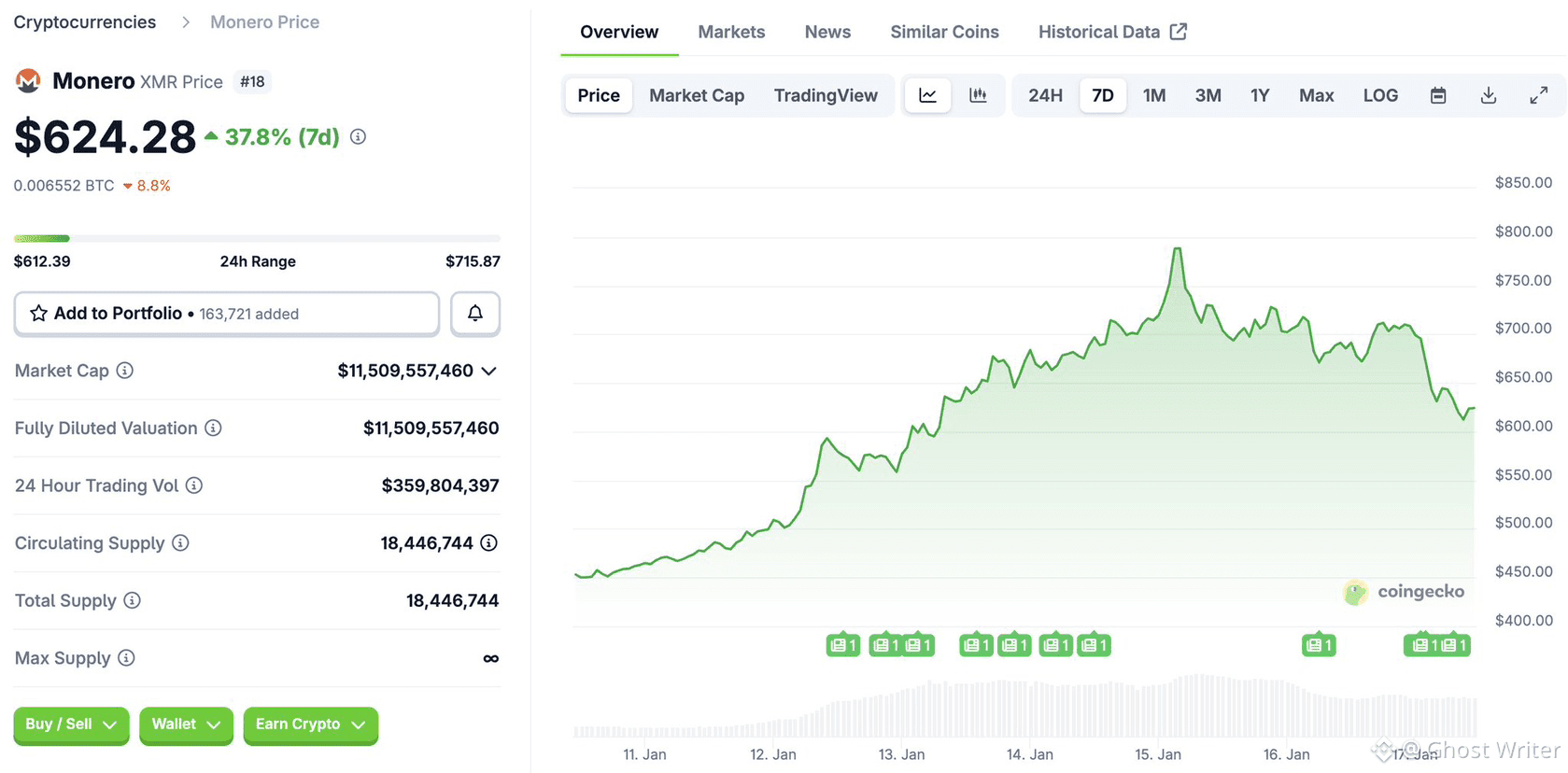
This case highlights how even cold-storage users remain vulnerable when social engineering bypasses the device itself. The attacker didn’t crack the hardware—they tricked the human.
Key lessons to stay SAFU on Binance (and anywhere):
1. Never share seed phrases or screen access — no matter who claims to be support, recovery service, or “Binance staff”. Official Binance never asks for seeds or remote control.
2. Enable every security layer
- 2FA (preferably YubiKey or authenticator app, not SMS)
- Anti-phishing code in Binance app/email
- Withdrawal address whitelist
- Device management (revoke unknown logins immediately)
3. Verify every link and message
Scammers clone Binance domains, emails, and even 2FA prompts. Always type binance.com manually or use bookmarks. Check sender domains carefully.
4. Keep large holdings diversified and offline
Hardware wallets are excellent, but pair them with multisig or split across cold/hot wallets. Avoid keeping life-changing sums on one device.
5. Use Binance SAFU features proactively
- Proof of Reserves → verify your assets are backed
- Insurance fund covers platform hacks (not user-side social engineering)
- Real-time withdrawal monitoring and suspicious activity alerts
Social engineering remains crypto’s #1 attack vector because it exploits trust, not code. The $282M loss wasn’t a Binance failure—it was a human one. Stay paranoid, stay skeptical, stay SAFU.
Protect your keys, verify twice, trust no one by default.
What’s your strongest security habit right now? Drop it below.

