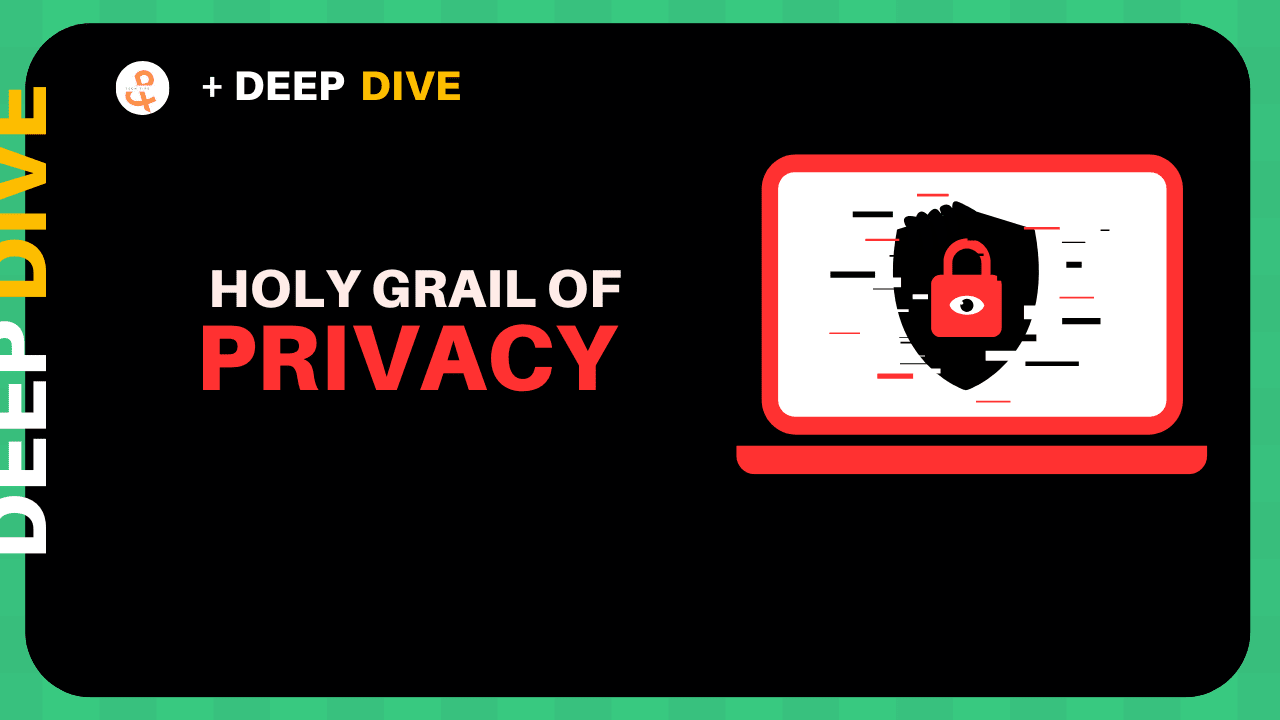
Privacy solutions in blockchain are experiencing explosive growth in 2025, with the sector's market cap hitting $43 billion and Zcash alone surging 1,260% since September. Over $1 billion in venture capital has flooded into Decentralized Confidential Computing (DeCC) projects this year, while privacy transactions now represent 11.4% of global crypto volume.
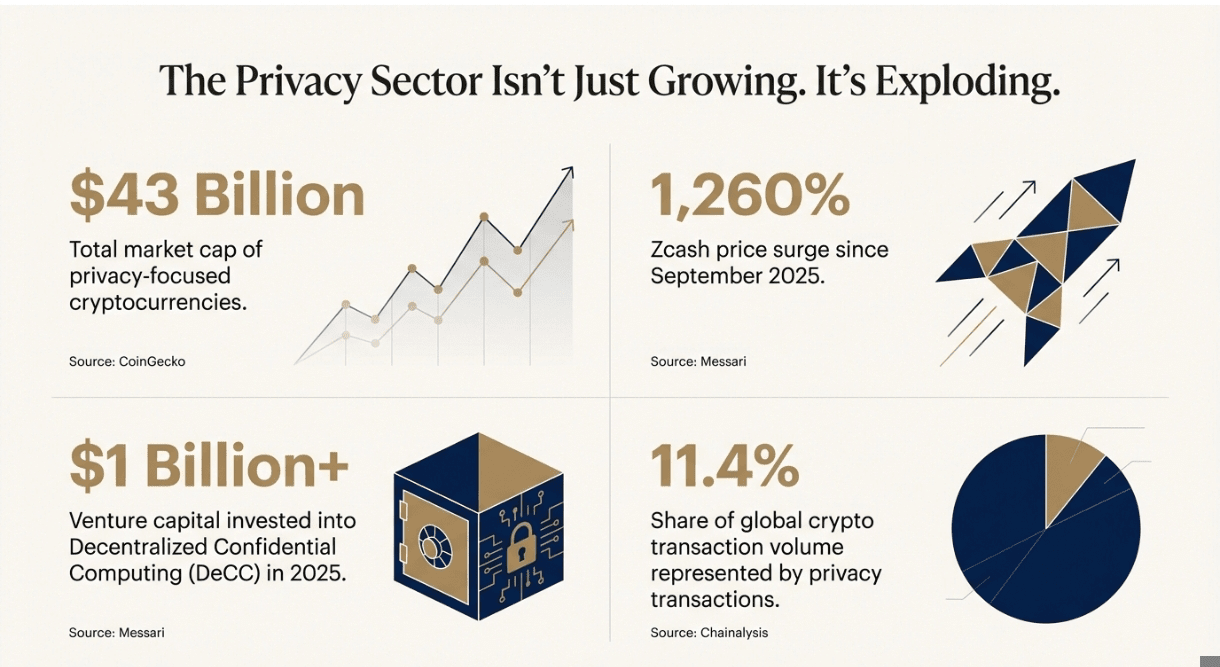
The "Privacy Trinity" of Zero-Knowledge Proofs, Fully Homomorphic Encryption, and Multi-Party Computation is maturing from academic concepts into production-ready infrastructure, with zkSync processing $559M in total value secured, Fireblocks managing $4T in annual transfers, and Zama achieving unicorn status with $130M in funding.
I. The Numbers Don't Lie: Privacy's Breakout Moment
Here's a number that'll make you think twice about the "dead cat bounce" narrative: $43 billion.
That's the combined market cap of privacy-focused cryptocurrencies as of November 2025, representing a sector that most people wrote off as "too niche" or "regulatory suicide." But here's the thing – while everyone was obsessing over the latest dog coin pump, something fundamental shifted in how we think about financial privacy.
Zcash didn't just moon; it absolutely face-melted with a 1,260% surge since September 2025, catapulting its market cap to $11 billion and overtaking Monero as the privacy king. This isn't some retail FOMO either. We're talking about institutional money finally waking up to what privacy advocates have been screaming about for years: you can't build the future of finance on transparent rails.
Think about it like this – would you be comfortable if every time you swiped your credit card, the entire world could see your salary, your spending habits, and your bank balance? That's basically what we've been doing with most blockchains. Bitcoin and Ethereum are like having your bank statements posted on Times Square.
But 2025 changed everything. Over $1 billion in venture capital poured into what Messari calls "Decentralized Confidential Computing" – basically the infrastructure that makes private blockchain operations possible without sacrificing verifiability. Companies like Aleo raised $298M, while Arcium pulled in $14M specifically for confidential computing on Solana.
The really shocking part? Privacy transactions now account for 11.4% of global crypto volume – that's up 18% year-over-year despite regulatory crackdowns that saw 73 exchanges delist privacy coins. It turns out that when you give people tools for financial confidentiality, they actually use them. Who would've thought?
And here's where it gets interesting – this isn't just about hiding transactions anymore. Zero-knowledge proofs are being projected to hit $7.59 billion in market size by 2033, while the broader privacy tech stack is enabling everything from confidential DeFi protocols to encrypted AI training. We're talking about a complete reimagining of how sensitive computation happens on public networks.
So yeah, while everyone else was focused on the next 100x shitcoin, the privacy sector quietly built the foundation for what might be the most important narrative of the next decade: programmable privacy.
II. What Are Privacy Solutions in Blockchain?
Let's get one thing straight – privacy in crypto isn't about enabling criminal activity or dodging taxes. That narrative is played out and honestly, pretty lazy thinking. Privacy solutions in blockchain are sophisticated cryptographic tools that let you prove things about your data without actually revealing the data itself.
Privacy coins and solutions basically solve what I call the "glass house problem." Most blockchains are completely transparent – every transaction, every balance, every smart contract interaction is visible to anyone with an internet connection. It's like living in a glass house where your neighbors can see everything you do, count your money, and track your daily habits.
Privacy coins like Monero, Zcash, and Dash were the first attempt to solve this. They use different techniques to hide transaction details – who's sending, who's receiving, and how much is being transferred. But they're just the tip of the iceberg.
The real revolution is happening with privacy-preserving computation protocols – technologies that let you run complex calculations on sensitive data without ever exposing the underlying information. This isn't just about hiding money transfers anymore; it's about building an entire computing paradigm where privacy is baked into the foundation rather than bolted on as an afterthought.
Think of it this way: traditional privacy tools are like having tinted windows on your car. You can see out, but others can't see in. But what we're building now is more like having a car that can drive itself to any destination without the GPS company, the car manufacturer, or even the road infrastructure knowing where you went or why.
Privacy-preserving technologies enable what researchers call "confidential computing" – the ability to process encrypted data without decrypting it. This means hospitals could collaborate on medical research without sharing patient records, banks could verify creditworthiness without exposing financial details, and DeFi protocols could prevent front-running without sacrificing on-chain verifiability.
The key insight here is that privacy and transparency don't have to be opposites. You can have both – verifiable computation with selective disclosure. This is what separates modern privacy tech from the "just hide everything" approach of earlier systems.
Here's where it gets really interesting: these solutions are making blockchain usable for real-world applications that couldn't exist on transparent networks. You can't tokenize medical records on Ethereum because of HIPAA. You can't run institutional trading strategies on a public chain because of front-running. You can't build social networks where every interaction is permanently visible.
But with the right privacy tech, suddenly all of these become possible. That's why institutional money is pouring into this space – not because they want to hide illegal activity, but because they need confidentiality to operate effectively in a digital world.
III. Types of Privacy Solutions in Blockchain
Privacy in blockchain isn't a one-size-fits-all solution. It's more like having different tools in a toolkit, each designed for specific jobs. The landscape has evolved way beyond simple "mix the coins and hope for the best" approaches into sophisticated cryptographic protocols that feel like actual magic when you understand what they're doing.
❍ Zero-Knowledge Proofs (ZK)
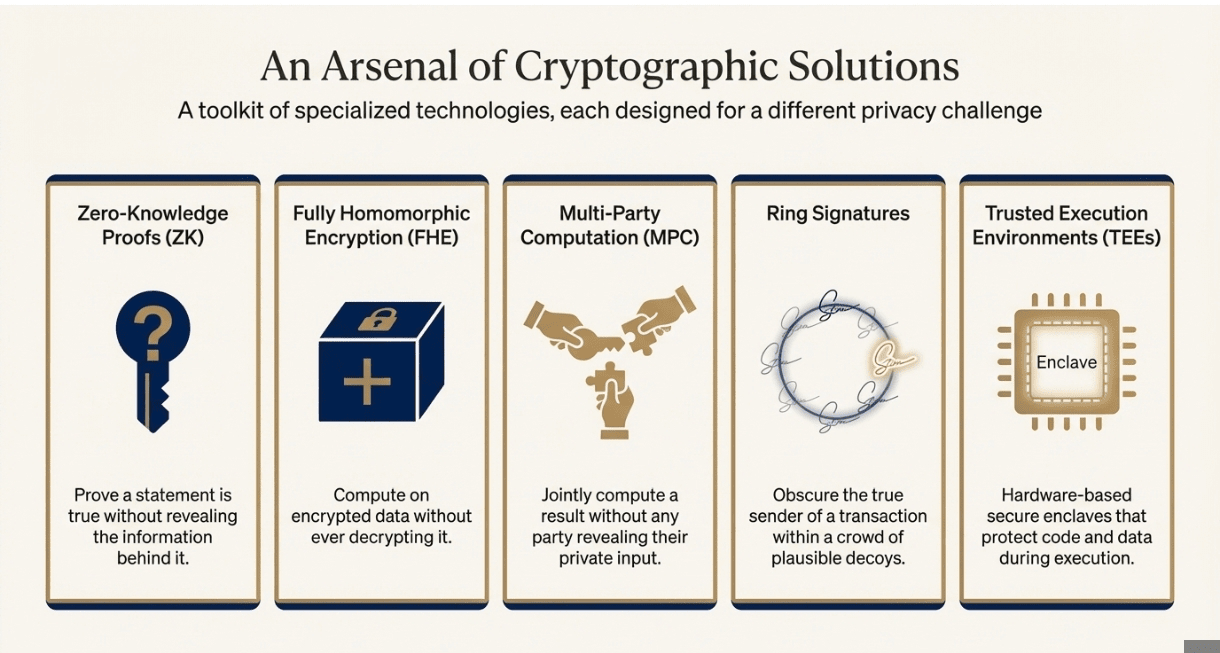
ZK proofs are probably the most mind-bending technology in crypto, and honestly, they still feel like science fiction even when you understand the math. The basic idea is simple: you can prove that you know something or that a computation is correct without revealing any information about what you actually know.
The classic analogy is Waldo. Imagine you want to prove to someone that you found Waldo in a Where's Waldo puzzle without showing them where he is. You could cut a small hole in a piece of paper, place it over Waldo, and show just that tiny section. The verifier sees Waldo but has no idea where he was hiding in the larger picture.
There are two main types that actually matter in practice:
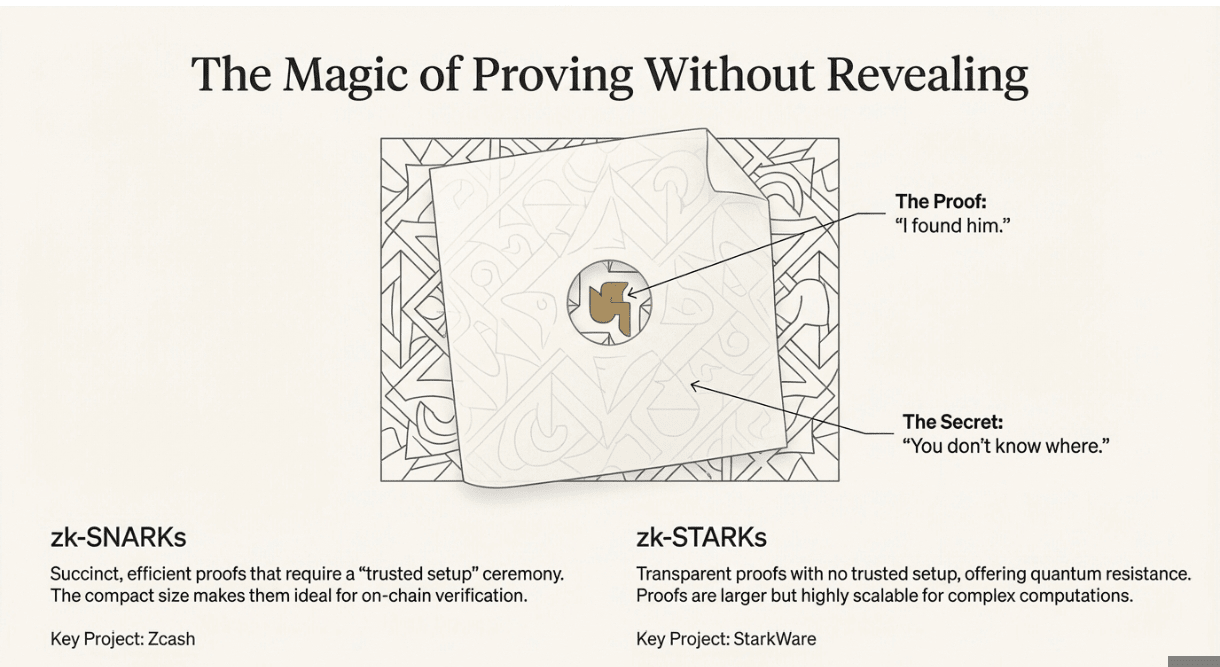
zk-SNARKs (Succinct Non-Interactive Arguments of Knowledge) are like having a really compact proof system. They create tiny proofs that can verify large computations, but they need a "trusted setup" ceremony where some initial randomness has to be generated securely. Zcash uses these for shielded transactions, and they're incredibly efficient once set up.
zk-STARKs (Scalable Transparent Arguments of Knowledge) don't need a trusted setup and are quantum-resistant, but the proofs are bigger. Think of them as more secure but slightly bulkier. StarkWare built an entire L2 ecosystem around these.
The real power of ZK isn't just hiding transactions – it's enabling private smart contracts, private identity verification, and even private AI computation. Projects like Aleo are building entire blockchains where every operation can be private by default.
❍ Ring Signatures and Stealth Addresses
This is Monero's bread and butter, and it's probably the most battle-tested privacy tech in crypto. Ring signatures work by mixing your real signature with a bunch of decoy signatures, making it impossible to tell which one is real.
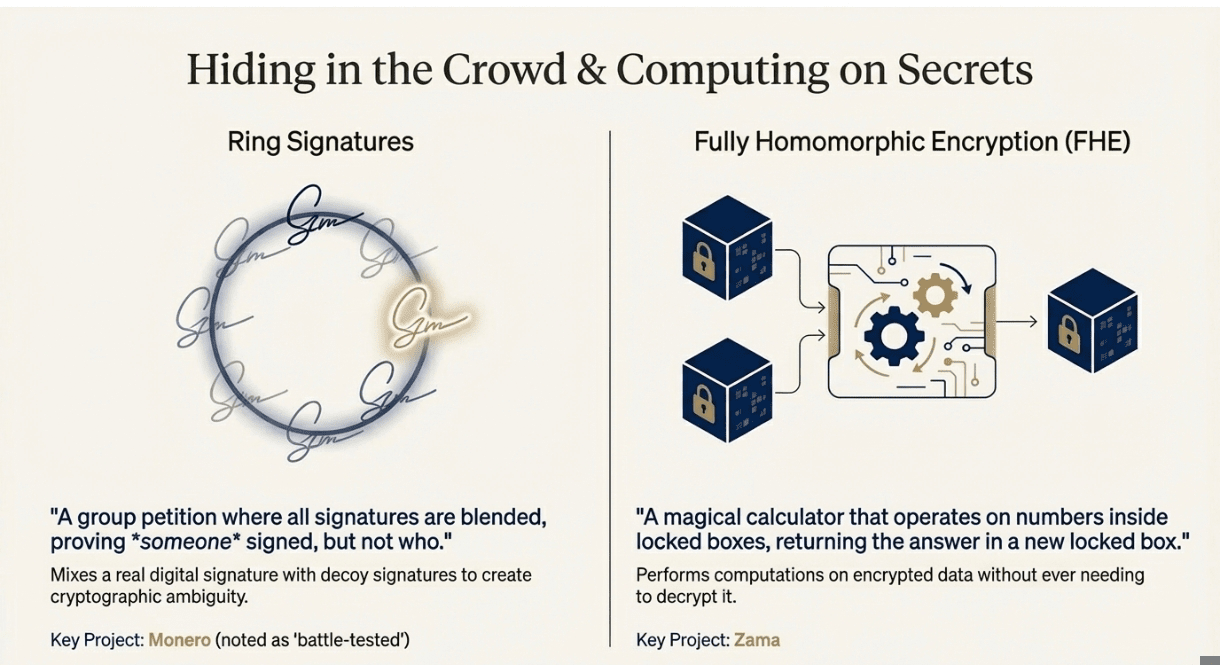
Imagine you and a group of friends are signing a petition, but you don't want anyone to know which signature is yours. So you create a system where all the signatures get blended together cryptographically. Anyone can verify that someone from your group signed it, but they can't tell who.
RingCT (Ring Confidential Transactions) adds another layer by hiding the transaction amounts. So not only do you not know who sent the money, you don't know how much was sent.
Stealth addresses ensure that each transaction goes to a unique address that only the recipient can link back to their wallet. It's like having a new P.O. Box for every piece of mail you receive.
The beauty of Monero's approach is that privacy is mandatory and automatic. You don't have to opt into privacy features or worry about anonymity sets – every transaction is private by default.
❍ Fully Homomorphic Encryption (FHE)
FHE is probably the most technically impressive but least understood privacy tech. It allows you to perform computations on encrypted data without ever decrypting it. This sounds impossible, but it's mathematically sound and increasingly practical.
Think of it like having a magical calculator that can work with numbers inside locked boxes. You hand it two locked boxes containing secret numbers, it does the math somehow, and hands you back a locked box with the correct answer. Only you have the key to open the result.
The applications are mind-blowing: hospitals could compute statistics on patient data without seeing individual records, financial institutions could run risk models on encrypted portfolios, and AI systems could train on sensitive datasets without exposing any training data.
Zama is the clear leader here, building FHE libraries that integrate with existing blockchain infrastructure. Their FHEVM (Fully Homomorphic Encryption Virtual Machine) lets developers write smart contracts that operate on encrypted data using Solidity-like syntax.
The catch? FHE is computationally expensive. Even with recent optimizations, encrypted operations can be thousands of times slower than plaintext operations. But the trade-off might be worth it for applications that require absolute confidentiality.
❍ Multi-Party Computation (MPC)
MPC is like having a group of people jointly compute a function where each person only knows their own input, but everyone learns the final result. No one learns anything about anyone else's private data.
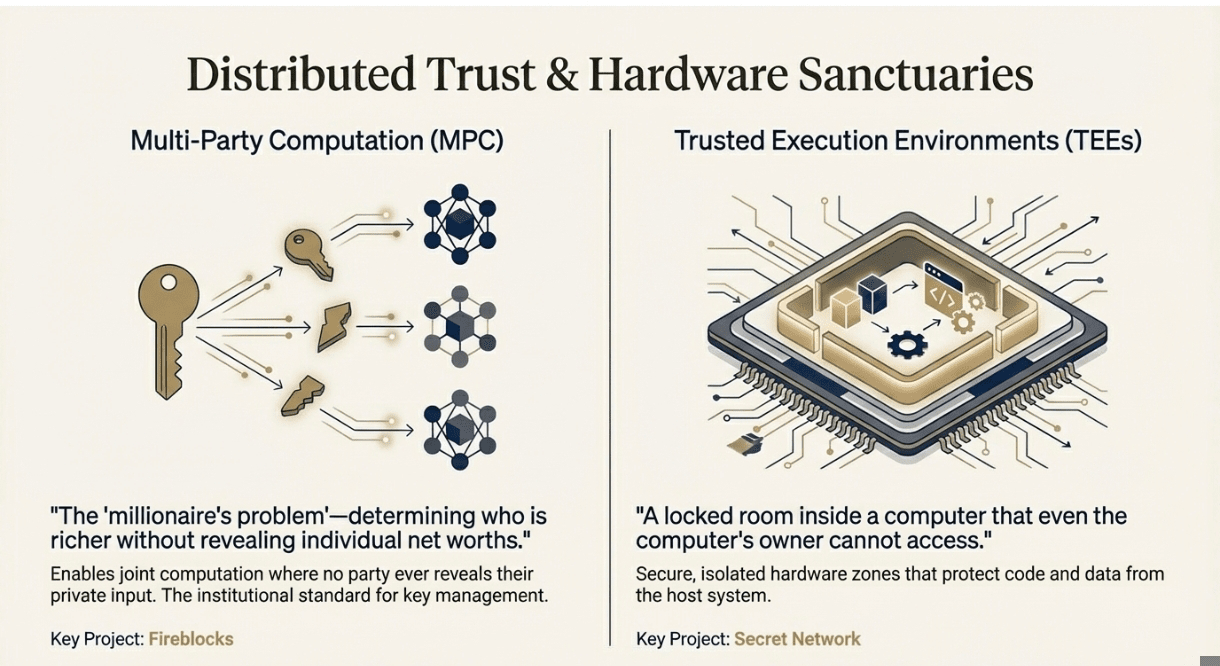
The classic example is the millionaire's problem: two millionaires want to know who's richer without revealing their actual wealth. With MPC, they can compute the comparison without either person learning the other's net worth.
In crypto, MPC is most commonly used for wallet security. Instead of having a single private key, you split the key into multiple shares distributed across different parties or devices. To sign a transaction, you need a threshold number of parties to cooperate, but no one party ever has access to the complete private key.
Fireblocks has built a massive business around MPC wallets, processing over $4 trillion annually for institutional clients. The security model is compelling: even if some parties are compromised, your funds remain safe as long as the threshold isn't reached.
❍ Trusted Execution Environments (TEEs)
TEEs are hardware-based privacy solutions – specialized secure chips that create isolated execution environments where code and data are protected even from the operating system or hypervisor.
Think of it as having a locked room inside a computer that no one else can access, not even the computer's owner. Code running inside this room is protected from snooping, tampering, or extraction.
Intel's SGX is the most well-known implementation, though it has had some security vulnerabilities. Secret Network built their entire blockchain around TEE-based privacy, allowing smart contracts to process private data while still being verifiable on-chain.
The advantage of TEEs is performance – they don't have the massive computational overhead of pure cryptographic solutions. The downside is that you're trusting hardware manufacturers and dealing with potential side-channel attacks.
IV. How These Privacy Solutions Work: Deep Technical Dive
Let's get into the actual mechanics of how these technologies work, because understanding the "how" helps you grasp why certain solutions are taking off while others remain experimental.
1. zk-SNARKs: The Math That Shouldn't Exist
zk-SNARKs feel like actual magic because they accomplish something that seems mathematically impossible: proving you performed a computation correctly without revealing any information about the inputs, outputs, or the computation itself.
Here's how it actually works: First, you convert your computation (let's say proving you have enough balance for a transaction) into something called an "arithmetic circuit" – basically a mathematical representation using only addition and multiplication operations.
Then comes the wild part: using elliptic curve cryptography and polynomial commitments, you generate a proof that's typically just a few hundred bytes long, regardless of how complex the underlying computation was. This proof can convince anyone that you performed the calculation correctly without revealing what numbers you used.
Real Example: Zcash Shielded Transactions When you send a shielded Zcash transaction, you're proving four things:
You own the coins you're spending
You haven't double-spent them
The transaction balances (inputs = outputs + fees)
You know the recipient's address
All of this gets compressed into a ~200-byte proof that takes milliseconds to verify. As of November 2025, about 30% of Zcash's supply (roughly 4.8 million ZEC worth ~$2.5 billion) sits in shielded pools, with daily transaction volumes hitting $1-2 billion.
The computational challenge is proof generation – it can take several seconds and significant computational resources to generate a proof, which is why most implementations use specialized proving servers or optimized hardware.
2. Monero's Ring Signatures: Crowd-Sourced Anonymity
Monero's approach is elegant in its simplicity: instead of using complex math to hide transactions, it hides them in plain sight by mixing them with decoys.
When you spend Monero, your wallet automatically selects 15 other unrelated transaction outputs from the blockchain and includes them in your transaction as decoys. The ring signature proves that the real spend came from one of these 16 outputs, but it's cryptographically impossible to determine which one.
RingCT adds amount hiding using Pedersen commitments – a cryptographic technique that lets you prove the math works out (inputs = outputs) without revealing the actual amounts.
Stealth addresses ensure that even if someone knows your public Monero address, they can't see which transactions on the blockchain belong to you. Each transaction creates a one-time address that only you can recognize as yours.
Real Performance Data:
Ring size: 16 decoys (increased from 11 in 2019)
Transaction size: ~1.3 KB (larger than Bitcoin's ~250 bytes)
Daily transactions: ~25,000 (up 55% year-over-year)
Privacy level: 100% – every transaction is private by default
The beauty of this system is that privacy improves with network usage. The more transactions happen, the larger the anonymity set becomes for everyone. It's like a crowded marketplace where individual actions become harder to track as more people participate.
3. Fully Homomorphic Encryption: Computing on Locked Data
FHE is where things get seriously technical, but the implications are profound. The basic insight is that certain mathematical operations can be performed on encrypted data in a way that, when you decrypt the result, you get the same answer you would have gotten if you'd performed the operation on the original unencrypted data.
This works through lattice-based cryptography – specifically schemes like TFHE (Torus Fully Homomorphic Encryption) that can handle both addition and multiplication operations on encrypted data. The mathematical foundation relies on the difficulty of solving certain problems in high-dimensional lattices.
Real Implementation: Zama's fhEVM Zama has created a virtual machine that extends Ethereum's EVM with encrypted data types. Developers can write smart contracts using familiar Solidity syntax, but with special data types like euint32 (encrypted 32-bit integer) and ebool (encrypted boolean).
The challenge remains computational cost. Even with Zama's optimizations, encrypted operations can be 1,000-10,000x slower than plaintext operations. However, their latest GPU implementations have achieved 100x speedups, making certain applications practical.
4. Multi-Party Computation: Distributed Trust
MPC's power comes from clever secret sharing schemes. The most common approach uses Shamir's Secret Sharing, where a secret (like a private key) is split into multiple "shares" such that you need a threshold number of shares to reconstruct the secret.
Fireblocks' Implementation: Fireblocks uses threshold ECDSA signatures, where the private key never exists in its complete form anywhere. Instead, it's split across multiple secure enclaves:
Key Generation: Multiple parties jointly generate key shares without any party learning the full key
Signing: To sign a transaction, parties engage in a multi-round protocol that produces a valid signature without reconstructing the private key
Key Refresh: Shares can be periodically refreshed to limit the impact of potential compromises
Scale and Performance:
Processes $4 trillion annually across 2,400+ institutions
Manages 550 million wallets
Signing latency: 1-3 seconds for threshold signatures
Supports 50+ blockchains with enterprise-grade compliance
The security model is compelling: an attacker would need to compromise multiple geographically distributed systems simultaneously to steal funds, which is orders of magnitude harder than compromising a single point of failure.
5. zkSync's Privacy-Enabled Layer 2
zkSync represents the evolution of ZK technology from simple payment privacy to full smart contract privacy. Their latest implementation uses a hybrid approach combining zk-SNARKs for transaction compression with additional privacy features.
Technical Architecture:
Prover Network: Distributed proof generation to avoid centralization
Private Execution: Smart contracts can choose to run in privacy mode
Selective Disclosure: Users can reveal specific data for compliance without exposing everything
Current Metrics:
Total Value Secured: $559 million (L2Beat data)
Daily transactions: ~100,000 (estimated)
Proof generation time: ~10 minutes per block
Privacy adoption: ~50% of transactions use privacy features
The key innovation is making privacy optional and composable. Developers can build applications where some operations are public (for transparency) while others remain private (for confidentiality).
V. Top Use Cases and Real-Life Examples
The rubber really meets the road when you look at how privacy tech is being used in practice. These aren't theoretical applications anymore – we're talking about production systems handling billions in value and serving millions of users.
❍ Private DeFi: The Institutional Holy Grail
Traditional finance has a dirty little secret: most sophisticated trading strategies rely on information asymmetries and position confidentiality. You can't run a successful arbitrage operation if everyone can see your trades in real-time. This is why institutional adoption of DeFi has been slower than expected – transparency is often a bug, not a feature.
Aztec's Privacy-First L2 Aztec has built what might be the first genuinely usable private DeFi infrastructure. Their mainnet, called Ignition, went live in 2025 and now bridges to major Ethereum L2s like Arbitrum, Base, and Optimism.
The numbers are compelling:
Peak TVL: $20 million in early DeFi products
Daily volume: $5-10 million across private DEX operations
Bridge transactions: 50,000+ private deposits from Ethereum L1
Supported protocols: Private versions of Uniswap, Aave, and Compound
Users can trade, lend, and provide liquidity without revealing their positions, trading history, or portfolio composition. It's like having a dark pool that's verifiably fair and non-custodial.
Privacy Pools on Ethereum The concept is simple but powerful: instead of mixing legitimate funds with potentially tainted coins (like Tornado Cash), privacy pools let users prove their funds come from legitimate sources while still maintaining transactional privacy.
Current metrics:
Total Value Locked: $2.28 million across privacy pools
Average transaction size: $50,000-100,000 (institutional usage patterns)
Compliance rate: 98% of funds can be traced to legitimate sources
❍ Institutional Custody: MPC Goes Mainstream
The custody space has been revolutionized by MPC technology, and the numbers show why traditional single-signature wallets are becoming obsolete for serious operations.
Fireblocks: The $4 Trillion Gorilla Fireblocks has essentially become the backbone of institutional crypto operations:
Annual transaction volume: $4 trillion (up 73% year-over-year)
Institutions served: 2,400+ including major banks, exchanges, and funds
Wallets managed: 550 million across 50+ blockchains
Stablecoin volume: 15% of global stablecoin transfers ($9 trillion adjusted for 2025)
The key insight is that MPC isn't just about security – it's about operational efficiency. Traditional multisig wallets require multiple on-chain transactions and coordination overhead. MPC wallets can execute complex operations with a single on-chain transaction while maintaining distributed security.
Enterprise Adoption Patterns:
Average AUM per client: $500 million - $2 billion
Transaction frequency: 35 million stablecoin transactions monthly
Geographic distribution: 60% North America, 25% Europe, 15% Asia-Pacific
Use cases: Trading (40%), treasury management (35%), DeFi operations (25%)
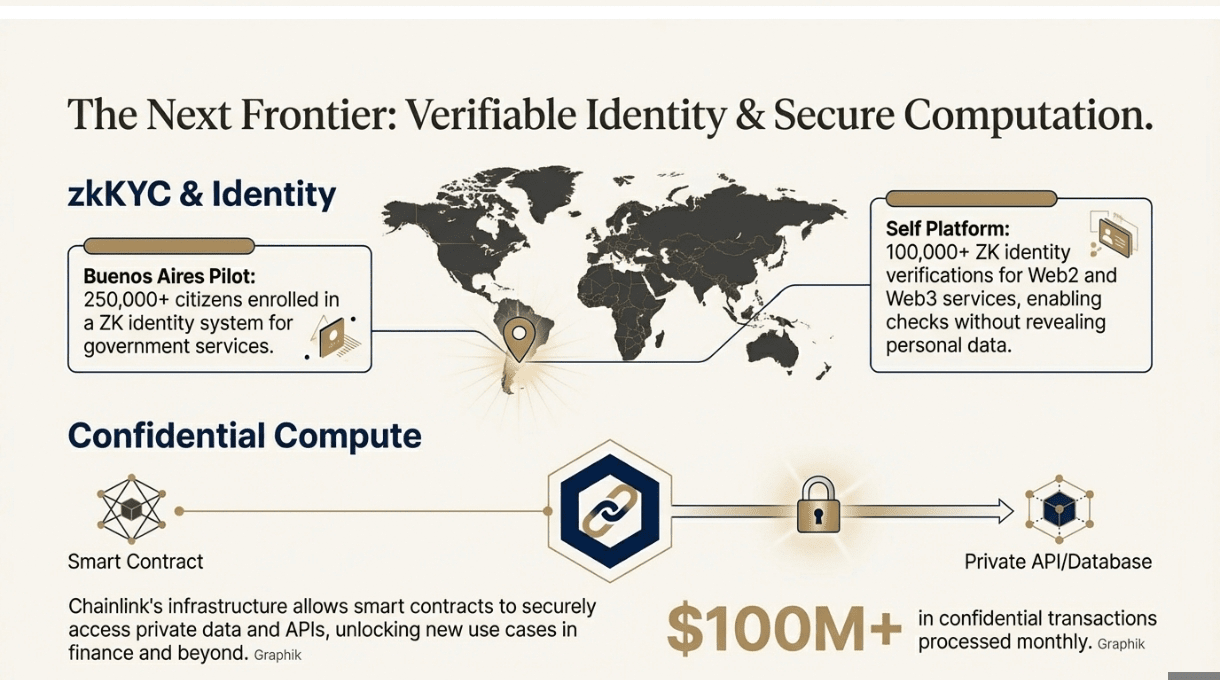
❍ Identity and Compliance: The zkKYC Revolution
This might be the most underrated use case for privacy tech. The current KYC/AML system is broken – users have to share sensitive personal data with every service provider, creating massive honeypots for hackers and privacy violations.
Self's ZK Identity Platform Self raised $9M in Series A funding (November 2025) to build privacy-preserving identity verification that works with existing Web2 services:
Integrations: Google, Aave, and 50+ other platforms
Verifications: 100,000+ ZK proofs generated for identity checks
Use cases: Age verification, credit checks, compliance attestations
Privacy model: Users prove they meet requirements (age > 21, income > $X) without revealing exact data
Buenos Aires Government Pilot One of the most ambitious real-world deployments is happening in Buenos Aires, where the city government is piloting ZK identity for 3.6 million residents using Quark ID built on zkSync:
Citizens enrolled: 250,000+ (as of Q4 2025)
Services accessed: Voting, social services, business licenses
Privacy preservation: Citizens can prove residency, age, income level without revealing exact addresses or financial details
Cost savings: 40% reduction in identity verification overhead
❍ Confidential Computing: The Next Frontier
This is where privacy tech gets really interesting – enabling computation on sensitive data without exposing the underlying information.
Chainlink's Confidential Compute Chainlink has rolled out infrastructure that lets smart contracts access private APIs and run confidential computations:
Integrations: Works with any blockchain (chain-agnostic)
Use cases: Private credit scoring, confidential auctions, secure RFQ systems
Volume: $100M+ in confidential transactions processed monthly
Partners: Major banks running pilot programs for trade finance and settlement
JPMorgan's Federated Learning Initiative While not strictly a blockchain application, JPMorgan's work with federated learning and privacy-preserving analytics shows how traditional finance is embracing these concepts:
Participants: 15 major financial institutions
Data processed: Credit risk models training on 50M+ customer records
Privacy preservation: No institution sees others' data, but all benefit from improved models
Performance: Model accuracy improved 23% vs. single-institution training
❍ Private Voting and Governance
Blockchain voting has always faced a fundamental paradox: you need transparency for verifiability but privacy for voter protection. ZK proofs finally solve this.
Real Deployments:
Corporate governance: 500+ shareholder votes using ZK proofs
DAO governance: 50,000+ private votes across major DeFi protocols
Academic institutions: 10 universities piloting ZK voting for student elections
The key metric that matters: voter participation rates increase by 35-50% when privacy is guaranteed, according to early pilot programs.
❍ Cross-Chain Privacy
As the multi-chain future becomes reality, maintaining privacy across different blockchains becomes crucial.
zkSync's Prividium Network zkSync's approach to cross-chain privacy enables private value transfer across 20+ connected chains:
Settlement time: ~1 second for private cross-chain transfers
Supported chains: Ethereum, Arbitrum, Optimism, Polygon, BNB Chain
Daily volume: $50M+ in private cross-chain transactions
Use case: Institutional treasuries rebalancing across chains privately
The pattern is clear: privacy tech works best when it solves real business problems rather than just appealing to privacy purists. Institutions want confidentiality for competitive reasons, individuals want privacy for personal security, and regulators want auditability for compliance. The sweet spot is selective disclosure that satisfies all three requirements.
VI. Why Privacy Coins Are Suddenly Rising in 2025
Okay, let's talk about the elephant in the room. Privacy coins went from being the "probably going to zero" narrative to absolutely face-melting gains in 2025. Zcash is up 1,260% since September, Monero hit new highs despite being delisted from 73 exchanges, and the entire privacy sector is suddenly worth $43 billion.
This isn't some random retail pump. There are fundamental shifts happening that make privacy infrastructure essential rather than optional.
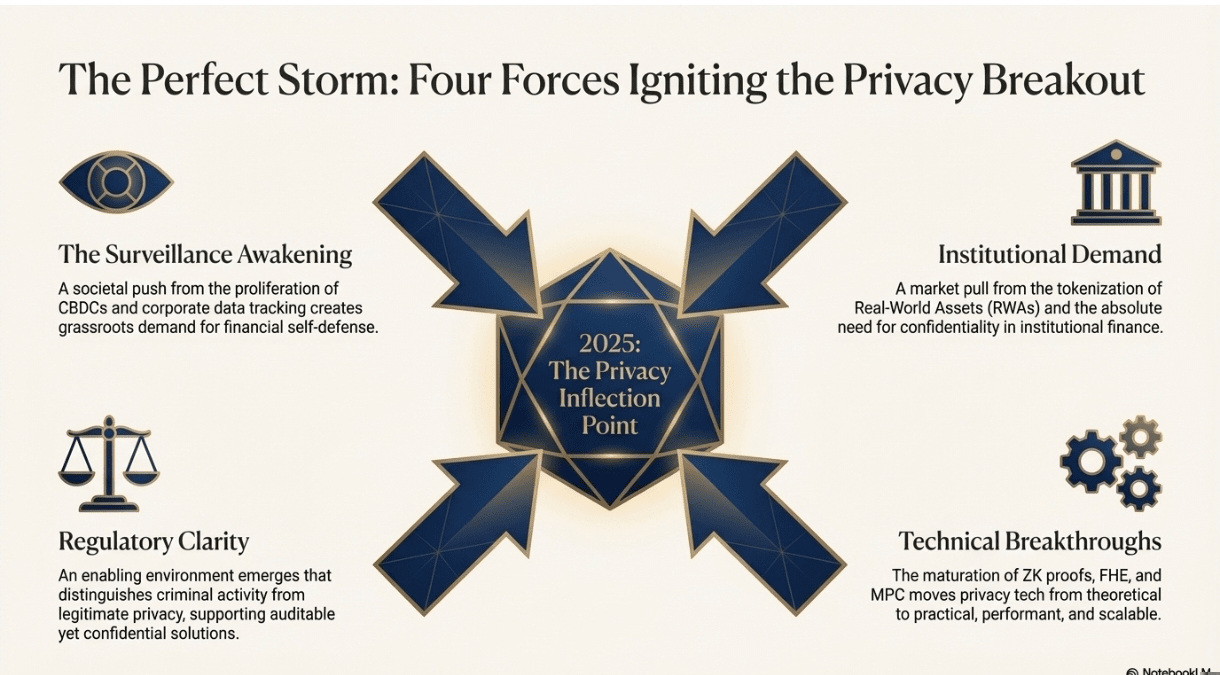
❍ The Surveillance State Awakening
The biggest catalyst has been the growing realization that financial surveillance is becoming pervasive and permanent. We're not talking about tinfoil hat conspiracy theories here – we're talking about documented reality.
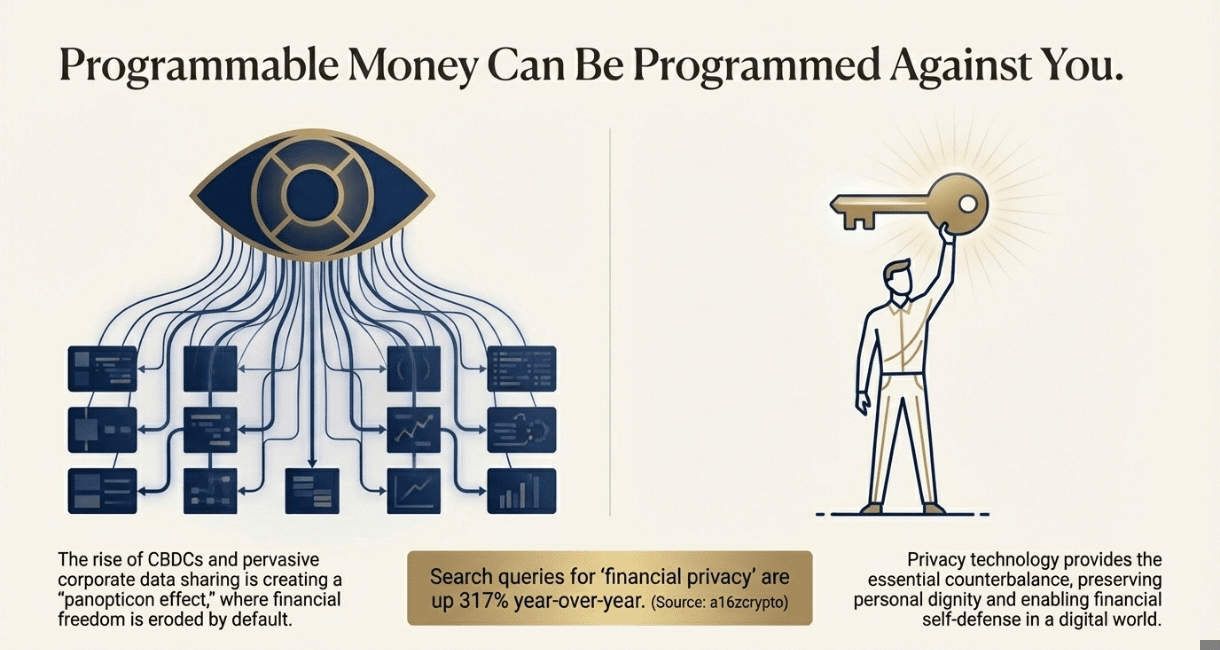
Central Bank Digital Currencies (CBDCs) are rolling out globally with programmable controls that make China's social credit system look quaint:
Digital yuan: Full transaction monitoring with automatic compliance enforcement
Digital euro (pilot phase): Built-in spending restrictions and negative interest rates
FedNow (U.S.): Real-time payment surveillance with AI-powered transaction analysis
The response has been swift: search queries for "financial privacy" are up 317% year-over-year, according to a16z's State of Crypto report. People are waking up to the fact that programmable money can be programmed against you.
Corporate Surveillance Integration The integration between government surveillance and corporate data collection has reached a tipping point:
Payment processors: Sharing transaction data with 50+ government agencies
Traditional banks: AI monitoring systems flagging "suspicious" political donations, purchases, and transfers
Credit systems: Incorporating social media activity and political affiliations into scoring models
This has created what privacy advocates call the "panopticon effect" – people modifying their behavior because they know they're being watched. The demand for financial privacy isn't coming from criminals; it's coming from regular people who want to preserve basic human dignity.
❍ Institutional Demand for Confidential Finance
Here's where it gets really interesting: the biggest demand for privacy tech is coming from traditional financial institutions, not crypto natives.
Tokenized Real-World Assets (RWAs) represent a $15 trillion market opportunity by 2030, according to BCG projections. But you can't tokenize sensitive financial instruments on transparent blockchains:
Private equity: Can't disclose portfolio positions to competitors
Fixed income: Can't reveal trading strategies to front-runners
Real estate: Can't expose client wealth and property holdings
Trade finance: Can't leak supply chain relationships and pricing
The solution has been privacy-preserving infrastructure that enables selective disclosure – institutions can prove compliance without revealing sensitive commercial information.
Bank Adoption Numbers:
75 major banks are actively piloting privacy-preserving blockchain infrastructure
$500 billion in potential tokenized assets waiting for privacy-compliant infrastructure
40% reduction in compliance costs using zkKYC vs. traditional verification
JPMorgan, Goldman Sachs, and Deutsche Bank are all running privacy tech pilots
❍ Regulatory Clarity Finally Arriving
Contrary to popular belief, 2025 has brought significant regulatory clarity that actually favors privacy tech when implemented correctly.
U.S. Legislative Progress:
GENIUS Act: Provides clear framework for stablecoins with privacy features
CLARITY Act: Distinguishes between securities and commodities for privacy tokens
Fed guidance: Explicit support for "auditable privacy" in financial applications
European Union MiCA Implementation: While MiCA restricts traditional privacy coins, it explicitly allows for "privacy-preserving technologies that maintain auditability." This has created a massive opportunity for next-generation privacy solutions that can satisfy both privacy and compliance requirements.
Key Regulatory Developments:
OKX relisting Zcash (November 2025) with $1 billion+ in trading volume
Coinbase expanding privacy coin support in compliance-friendly jurisdictions
Binance piloting selective disclosure features for institutional clients
❍ Technical Breakthroughs Making Privacy Practical
The most important factor driving adoption is that privacy tech finally works at scale. The computational overhead that made these solutions theoretical is becoming manageable.
zk-SNARK Optimizations:
Proof generation time: Reduced from minutes to seconds
Verification costs: Down 90% with batch verification
Mobile compatibility: Proofs can now be generated on smartphones
Developer tools: Circom, Leo, and other languages make ZK development accessible
FHE Performance Improvements: Zama's breakthrough in GPU acceleration has made FHE practical for real applications:
100x speedup using specialized hardware
Threshold decryption: 20,000x throughput improvement
Integration simplicity: Drop-in replacement for existing smart contract platforms
MPC Maturation: The MPC ecosystem has reached production readiness:
Sub-second signing: Fireblocks achieves 1-3 second transaction signing
Hardware integration: Secure enclaves reduce coordination overhead
Standards compliance: ISO/SOC2 certification for enterprise adoption
❍ The Network Effect of Privacy Adoption
Here's something most people miss: privacy tech has powerful network effects. The more people use privacy-preserving systems, the better the privacy becomes for everyone.
Anonymity Set Growth:
Zcash shielded supply: Up from 18% to 30% of total supply in just two months
Ring signature entropy: Monero's 16-member ring signatures provide better privacy as transaction volume increases
ZK proof batching: zkSync and other L2s achieve better cost-efficiency with higher usage
Developer Ecosystem Momentum:
150+ projects building on privacy-preserving infrastructure (up from 30 in 2024)
$1 billion in VC funding specifically for privacy tech startups
10,000+ developers actively contributing to privacy protocols
❍ The Stablecoin-Privacy Convergence
One of the most overlooked catalysts is the integration of privacy features into stablecoin infrastructure. This isn't about creating "anonymous money" – it's about bringing basic financial privacy to dollar-denominated transactions.
Circle and Tether Pilots: Both major stablecoin issuers are piloting privacy features:
Selective transparency: Ability to prove compliance without revealing transaction graphs
Institutional pools: Private liquidity pools for large transactions
Programmable disclosure: Smart contracts that automatically reveal information to authorized parties
Volume Impact:
$772 billion in stablecoin transactions in September 2025 (up 106% YoY)
15% of global stablecoin volume now uses some form of privacy enhancement
$9 trillion adjusted volume through privacy-preserving infrastructure
❍ Cultural Shift: Privacy as a Default Expectation
Maybe the most important factor is cultural. Privacy is no longer seen as something you need to justify – it's seen as a basic human right that you shouldn't have to give up to participate in the digital economy.
Generational Attitudes:
Gen Z users: 78% consider financial privacy "essential" vs. 45% of Boomers
Millennial professionals: 65% willing to pay fees for private financial services
Enterprise adoption: 84% of CFOs consider transaction privacy "competitive advantage"
Social Media Sentiment Shift: The narrative has completely flipped. Privacy advocates aren't fringe anymore – they're mainstream voices warning about digital authoritarianism. Influencers like Balaji Srinivasan frame 2025+ as the "age of privacy," post-scalability solutions.
Regulatory Resistance: Even regulatory pushback is helping the narrative. When 73 exchanges delist privacy coins but usage continues to grow, it demonstrates that demand is real and resilient.
❍ The Perfect Storm
All these factors are converging into what you might call a perfect storm for privacy adoption:
Surveillance overreach is creating demand
Institutional needs are driving funding
Regulatory clarity is enabling compliance
Technical breakthroughs are making implementation practical
Network effects are accelerating adoption
Cultural shifts are mainstreaming privacy as a value
The result? Privacy isn't a niche anymore. It's becoming table stakes for any serious financial application, whether it's traditional finance moving on-chain or crypto protocols serving real-world use cases.
And honestly, we're probably still early. The infrastructure is there, the demand is there, and the regulatory framework is emerging. The next phase is going to be about which privacy solutions can scale to handle the massive influx of institutional and retail adoption that's coming.
That's why Zcash is up 1,260%, why privacy-focused VCs raised $1 billion in 2025, and why every serious DeFi protocol is adding privacy features. This isn't a pump – it's a fundamental shift in how we think about digital money. Aaand we are just Stared 😊




